This is a timeless concept from roman times, passed down in popular culture, and can be applied to your business information systems security plan. Companies of even modest size and complexity rely on some form of IT to support their computer systems and data. Although, most companies trust their IT department or Managed Services Provider to include security as a baseline component of their work, how do you verify your IT security is dong what you THINK it is doing? A Risk Assessment is a valuable tool.
Trust but verify.
“Fidete, sed verificate” is a famous Latin phrase: Trust but verify. You trust your IT department is doing their best when it comes to the security of your key computer systems and valuable data. However, when you think about their mission coupled with the rapidly increasing number of threats, it is better to exercise the “trust but verify” axiom.
Have you asked your IT department how they verify the security controls they manage? Are your IT security controls configured correctly and doing the job? It is a frightening thought to consider that most network breaches are discovered 146 days after the breach occurred1.
Most companies that suffer a network breach discover it months after the breach occurred.
What do Security Audits and Financial Audits have in common?
It is common practice to have annual financial audits completed by a third party. The ideal engagement for a Security Audit is when a third party partners with your existing IT person/department/MSP to validate what is being done and comprehensively reviews your security controls from start to finish. This is more likely to provide an unbiased and valuable assessment. The process must avoid any “blame game” mentality and sincerely understand how difficult it is to consistently configure and manage security controls. A Security Consultation and Security Audit makes financial sense – it gives you the data to make informed decisions on how to invest to best meet the security needs of your business and not waste money.
The Risk Assessment
Typically, The Risk Assessment is a key component of IT Security verification; however, there is much more to this than simply running a scanning tool once a month or answering a list of questions. The process must evaluate all the layers of security, including physical, technical, and administrative controls, identify gaps that exist, and provide real steps that can be taken to improve the overall security defenses that protect your computer systems and data.
The Risk Assessment is a comprehensive engagement of not only internal and external network scans but examining patching success, particularly third-party patching which many businesses struggle to keep current2; Comparing your documented policies with what you are doing and with best practices in crucial areas like password management, the principle of least privilege, and validation of other security mechanisms implemented at your business; Addressing your compliance regulations (ex. HIPAA, PCI, SOC2, CMMC, NIST, Cyber Insurance).
As a result of your Risk Assessment, you should have a comprehensive technical report, asset report, threat identification, prioritized gap analysis and a plan of action for remediation of any vulnerabilities or compliance gaps, and an executive briefing to summarize your overall security posture.
For most businesses, a full Risk Assessment should take place yearly. Additional Internal and/or External Vulnerability Scan may be needed to validate the integrity of your network when changes occur in your environment. Those under compliance or increased security needs, ongoing security monitoring and recurring audits of compliance are often required.
The Layers of Data Security
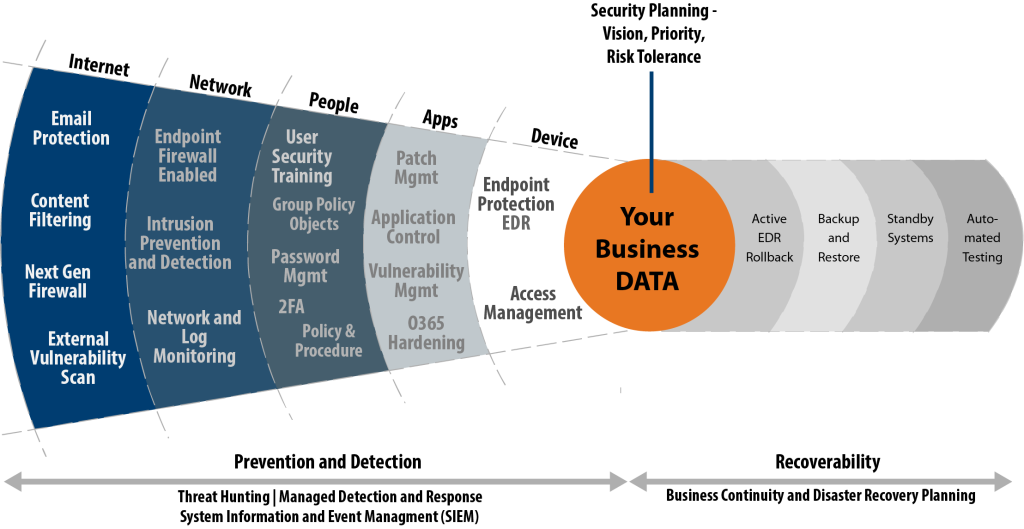
The AME Group Security Services Team believes Risk Assessments should do much more than provide an automated scan of your network.
The AME Group believes a comprehensive approach to performing the assessment provides actionable information to the IT department, the business management team, and executive leadership. Our process identifies gaps that exist in current controls and will detail recommendations on prioritization and actions to close those gaps.
Let our years of expertise add another level of safety to your business processes.
The AME Group Security Services Team provides a level of independence between the staff that configures and maintains a network from the staff that assesses and audits the security of that same network. Whether it is a consulting engagement, stand-alone project, or monthly recurring services, The AME Group Security Services Team is well-prepared to assist you.
Security Services
Risk Assessment
- Point in Time Review of Current Security and Compliance Posture
- Asset Identification
- Threat Identification
- Vulnerability Scans: Internal and External
- Controls Assessment: Physical, Technical, Administrative
- Gap Assessment, Prioritization for Remediation
Business Continuity and Disaster Recovery Planning
- Business Impact Assessment
- Recovery Point Objective: Backup Strategy
- Recovery Time Objective
- Table Top Exercises
Compliance Assistance
- Prepare and assist your organization to achieve desired compliance requirements
- Recurring evaluation of your environment against your specific compliance requirements
- NIST Cybersecurity Framework for environments without other regulatory requirements
- Recurring Security Risk Assessment
- Policies and Procedure Guidance
- Weekly and Monthly Reviews
Employee Security Awareness Training
- Annual Security Training
- Recurring Training on Relevant Security Topics
- Email Phishing Campaigns as a Training Tool
- Dark Web Breach Assessment
Incident Response Planning
- Response and Remediation plans
- Communications and Management
- Lessons Learned
Virtual Chief Information Security Officer
- Establish your Security Vision and Strategy
- Determine and Prioritize Security Initiatives (budget, schedule, resource allocation)
- Reduce Risk with Ongoing Security Improvements (project oversight)
1* https://www.infocyte.com/blog/2016/7/26/how-many-days-does-it-take-to-discover-a-breach-the-answer-may-shock-you
2* https://www.scmagazine.com/unrelenting-rise-in-vulnerabilities-risk-based-security-reports/article/664700/

