Sites are hacked every day.
- There is an attack every 39 seconds (Security Magazine)
- Hackers steal 75 records every second (Breach Level Index)
- More than 23 million people use the password ‘123456’ (National Cyber Security Centre)
- Traditional firewall and antivirus security is irrelevant and obsolete (Thycotic.com)
- Hackers create 300,000 new pieces of malware daily (McAfee)
- On average 30,000 new websites are hacked every day (Forbes)
Your Information IS for sale on the DarkWeb. It travels quickly across the world and is viewed by thousands in a weeks’ time[1]. Once on the internet, whether on the surface internet (what we know of as the internet) or on the deep/dark web, you cannot erase it. Many evil things happen on the dark web, it’s not just about stolen credentials. Drugs are sold; people are sold; counterfeit money is sold; access to your server is sold. Your stolen PII / PHI can be used to create what looks like a “real person” or to steal your actual identity to open credit card accounts, or even get healthcare.
So, You should behave as if your information is compromised.
If you do not know your Dark Web Status – contact us for a free scan.
Many breaches are not publicly disclosed, but your information is still on the Dark Web, for sale.

It’s hard to change your email, address and phone number, so that is not the plan. Focus on being aware of breaches and strengthen your password strategy.
MUST-DO Practices
Minimize the impact of the Dark Web having your email by avoiding the use of your WORK email on websites, unless necessary.
CHANGE that compromised password where-ever it, AND ANY VARIATION of it, is being used. When you take inventory, you will be surprised at how many logins your have created with the same password. They add up quickly.
- Use LONGER passwords, like phrases or a combination of several unrelated words.
- Use a unique password for every website or app login. To be able to do this, you need a password management app.
- Use a password manager, like LastPass, and get it to create long (14-16 characters), complicated passwords. You only have to remember the ONE that gets you into the app. Have I Been Pwned has a partnership with a management app called 1 Password, which is also a good app to use.
Use 2 FA (2 Factor Authentication). They have your login and password, but they don’t have your phone that gives you a 1-time use passcode to complete your login credentials. Many programs and websites have this as an OPTION, turn it on.
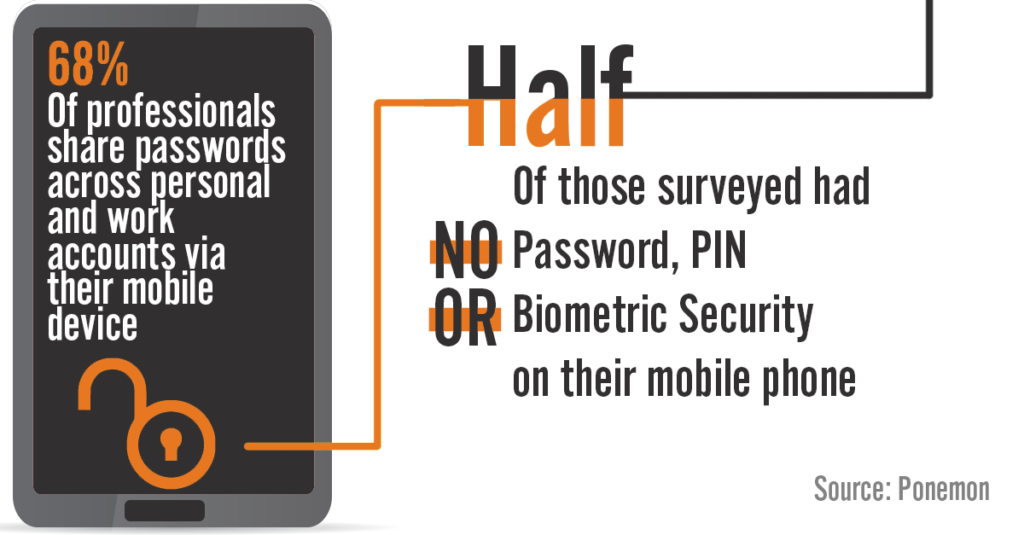
Other great practices:
Monitor for breaches. Some think this is controversial. If you assume your credentials are compromised and act accordingly, what will monitoring do to protect you? Our point of view is – you cannot ALWAYS be “on” AND on average, compromised credentials are not reported until 15 months after the breach occurs. Monitoring for identity theft and monitoring the Dark Web helps alert you immediately, which gives you the power to react more quickly and not wait until you remember to review ALL your vulnerabilities. A faster response to incidents is proven to lessen the impact, so why not, it is not very costly.
Business level monitoring – The Dark Web Breach Assessment included within The AME Group’s Breach Prevention Platform monitors up to 3 domains (ex. theamegroup.com) and sends alerts when something new is posted. All staff can also monitor their personal email address since they are often intertwined in business.
Personal level monitoring – the website “Have I been pwned”, shows you what type of data is found based on an email address. This is free. Many have received free Identity Theft monitoring from a company involved in a breach, like Equifax and Anthem. You can subscribe to this type of monitoring through IdentifyForce, LifeLock, or ID WatchDog. Prices for individual monitoring range from $120 – $300/year.
https://myaccount.google.com/security-checkup
Monitor your credit card and bank accounts regularly. With the great convenience of auto-pay, it’s easy to not look at accounts for months. Set appointment reminders to do so monthly.
File your taxes early before a criminal does it for you.
Review your credit history 2-3 times a year. You have one free report per year from the three agencies, use them 1 at a time and stagger your reviews.
https://www.annualcreditreport.com
- After the enormous breach of Equifax[2], many people have frozen their credit, so criminals cannot try to open accounts with your stolen information.
https://www.identitytheft.gov/Info-Lost-or-Stolen
https://www.consumer.ftc.gov/articles/0497-credit-freeze-faqs
- If you think your identity is stolen, report it immediately. Notify your banks and credit cards.
https://www.identitytheft.gov/
Do not use PUBLIC WIFI – it’s an easy target for criminals to intercept your activity. Just wait for a secure connection or get a hot-spot for business use.
[1] The experiment conducted by security vendor BitGlass
[2] 143 million Americans data was compromised in the 2017 Equifax breach

