April 25, 2024
As technology gets better, lots of businesses, like yours, are using Software-as-a-Service (SaaS) apps because they’re flexible, affordable, and easy to use. These cloud services are super popular in the business world. They offer all sorts of tools, from email and communication apps to customer management and project trackers. But while SaaS is great for making things easier, it also brings new challenges, especially when it comes to keeping your data safe. That’s why finding the right SaaS backup is not just a choice, but really important for protecting your
April 17, 2024
Hey, don’t let these myths about the security of your cloud applications put your business at risk! The cloud is a valuable tool for businesses. Most of you already have cloud-based applications and services. Now is the time to take a look at cloud security. Let’s clear up some common misconceptions: Myth 1: My cloud applications are completely secure. While leading SaaS solutions like Office 365, G Suite, and Salesforce do offer top-notch cloud application security and recovery features, they’re not completely foolproof. They can’t always protect your data from
April 17, 2024
We want to make you aware of a current ongoing attack against remote VPN connections for firewalls. Details can be found on the Cisco Talos threat intelligence website at https://blog.talosintelligence.com/large-scale-brute-force-activity-targeting-vpns-ssh-services-with-commonly-used-login-credentials/. Our SIEM log aggregation has recorded more than 2x the normal failed VPN login attempts in the past few days and can confirm this is an active attack campaign. The AME Group’s Security Team is actively monitoring our Managed Security Services clients for Indicators of Compromise to provide early warning and response to contain any potential compromise. Managed Internet Security
March 25, 2024
At The AME Group, our approach to client management goes beyond fixing immediate issues. It’s about building a long-term partnership focused on protection and productivity enhancement through technology. When a new client joins us, our first step is to stabilize their IT infrastructure and network. This ensures a strong foundation for future growth. Then we focus on business IT strategy during quarterly business reviews. Enhancing Business Productivity and Security Through Quarterly Business Reviews The Quarterly Business Review (QBR) is a key component of our client success process. Every quarter, we
February 29, 2024
Windows 10 end of life is October 14, 2025. The current version, 22H2, will be the final version of Windows 10. Risk of running Windows 10 after October 14, 2025 Once a product reaches the end of support, or a service retires there will be no new security updates, non-security updates, or assisted support. Therefore, your Windows 10 devices will not be as safe and effective. Your Windows 10 devices will be: · open to cyber-attacks. · more likely to experience poor performance. · unable to be repaired. Even with all
February 20, 2024
It is common to find inadequate cyber liability insurance policies. It is common to find businesses that think they are fully protected. Here’s how you can be confident in your cyber insurance coverage, find the best premium, and reduce your risks. EVERY WEEK, AT LEAST ONE BUSINESS CLAIM SURPASSES $1 MILLION* IDENTIFY EXPOSURE ROADMAP RISK MANAGEMENT OPTIMIZE CYBER COVERAGE HOW TO MAKE CYBER LIABILITY INSURANCE EASY The AME Group recommends FifthWall Solutions, a cyber insurance wholesaler fully dedicated to cyber liability and technology errors and omissions insurance (e & o).
February 14, 2024
In today’s interconnected world, businesses face a constant threat from cyber-attacks. To mitigate these risks, many organizations are turning to cybersecurity rating services like SecurityScorecard and BitSight. These services provide an independent assessment of a company’s security posture. This helps them understand their vulnerabilities and take proactive measures to protect their assets. Cybersecurity rating services use a range of data points to evaluate a company’s security posture. These include information about the company’s network security, DNS health, patching cadence, IP reputation, application security, and more. By analyzing these factors, these
February 13, 2024
What is the Best Practice Security Evaluation? It is a low-cost, high value evaluation of your business network and Microsoft 365 tenant. It will identify the current state of your IT systems by scanning the interior and exterior of your network. You will identify the most common security risks related to your business network, active directory, backups, Microsoft 365, users and endpoints. You will also identify the most common administrative security risks. Who delivers the Best Practice Security Evaluation? Our local engineer and strategic advisor deliver the service – the
February 06, 2024
The AME Group is a nominee in Smiley Pete’s Best of Lex! You get to vote on your favorite businesses and attractions in the great city of Lexington, KY! Would you please support us by voting for The AME Group? Here’s a link to the technology services section. There are a lot of other things you may want to vote for also. Smiley Pete’s Best of Lex https://bestoflex.smileypete.com/services/best-technology-firm VOTING ENDS FRIDAY Vote for The AME Group Best of Technology Services, Lexington, KY!
December 28, 2023
We speak often about cybersecurity risk. WHY? The cybersecurity landscape is dynamic. Attackers change their tactics to adapt to new security controls and new vulnerabilities. Acknowledging this reality reinforces the need for ongoing vigilance and adaptability in your cybersecurity approach. Eliminating cybersecurity risk is not possible. So, is cybersecurity hopeless? Not at all. There are powerful strategies that can help. Acknowledging this reality reinforces the need for ongoing vigilance and adaptability in your cybersecurity approach. Addressing the most critical security gaps, threats and vulnerabilities gives you a great return on
December 13, 2023
The AME Group is a leader in providing a comprehensive yet adaptive approach to securing your business. Our approach is COMPREHENSIVE, as anything less will fail to achieve the objective.Our approach is ADAPTIVE to both YOUR risk tolerance and to the constantly evolving threat landscape as it must be to be effective. Securing your business requires a multi-layered approach that addresses every potential attack vector > Devices, Apps, People, Process, Network, Internet, Email, etc. A comprehensive approach must factor in – Compliance requirements, and Your businesses objectives and expectations around
October 25, 2023
The choice of computer hardware can significantly impact productivity, security, and overall operational efficiency. While the idea of buying home computers for business environments may seem cost-effective, this paper argues against such a decision. It highlights the hidden costs of with home computers, the value of standardization in computer hardware, and the critical importance of data security. We aim to demonstrate that opting for business-grade computers is the prudent choice for a sustainable and secure business environment. We will discuss the disadvantages of home computers in a business setting are
October 19, 2023
The AME Group ranks among the Top 250 MSSPs for 2023, according to MSSP Alert, a CyberRisk Alliance resource. The Top 250 MSSPs (Managed Security Services Provider) honorees were announced in a live webcast on September 14. 📃The complete list and research report are available here: https://www.msspalert.com/top-250 🕛The on-demand webcast will be available to watch here: https://www.msspalert.com/webcasts Key findings include: MSSP Revenue Growth & Financial Performance: MSSP honorees, on average, expect to generate $56.3 million in revenue for 2023, more than double the number from our 2022 report. However, the
October 16, 2023
When we think of cyberattacks on electrical coops, we think of taking down our electrical grid. Operational technologies are modernized for efficiency and safety, but your electrical coop’s greater cyberthreat is what plaques other industries and businesses – data theft, fraud, ransomware. Is your IT side keeping up with the criminal’s strategies? In a recent West Monroe survey, 67% of utility leaders cited cybersecurity as their top concern of their converged IT and OT network. What strengthens all businesses is talking about cybersecurity. The Colorado electric coop, DMEA, did just
September 05, 2023
The AME Group ranks among the world’s Top 100 Vertical Market MSPs (http://www.channelE2E.com/top100) for 2023, according to ChannelE2E, a CyberRisk Alliance resource. The annual list and research report identify and honor the top 100 MSPs in healthcare, legal, government, financial services, manufacturing and additional vertical markets. Additionally, this year’s report revealed key MSP business, security and market trends and affirms that vertical market MSPs have vastly expanded their managed security capabilities. The AME Group ranked in the Top 5 Manufacturing MSPs. In addition to managed IT services, backup and recovery,
August 28, 2023
Small and medium-sized businesses opt for cloud solutions more often. Cloud computing delivers services over the Internet. So, instead of keeping your data on a hard drive or a flash drive, you can save it in the cloud and access it with a Wi-Fi connection. Here are a few benefits of cloud-based storage for small and medium businesses that you can take advantage of. Be Flexible and Pay by What is Used. With traditional data storage, you need to pay for hardware, infrastructure, and maintenance. As the saying goes, it’s
August 22, 2023
While the internet provides endless opportunities for learning, socializing, and self-expression, it also exposes students to various risks. And cyberbullying is one of the most prevalent risks present. Have you seen signs your child is being cyberbullied? As parents or adults with children in our lives, it is our responsibility to create a safe online environment for our children and equip them with the necessary tools to stop cyberbullying. Teach Kids Not to Cyberbully Open communication: Encourage your child to talk openly about their online experiences. Establish a supportive environment
August 22, 2023
While the internet provides endless opportunities for learning, socializing, and self-expression, it also exposes students to various risks. And cyberbullying is one of the most prevalent risks present. As parents or adults with children in our lives, it is our responsibility to create a safe online environment for our children and equip them with the necessary tools to combat and navigate cyberbullying. Watch out for these five signs your child is being cyberbullied. Emotional changes: Keep an eye out for sudden shifts in your child’s behavior, including increased irritability, sadness,
August 17, 2023
As another school year approaches, it’s essential for parents to not only focus on buying school supplies and organizing schedules but also on safeguarding their children’s online activities. Cybersecurity is an ongoing concern, and students can be particularly vulnerable to the risks online. Take proactive steps to educate and protect your student’s online presence, so that you can ensure their safety and provide them with a secure environment for learning. Here are some practical tips for parents to consider as their children head back to school: Strong Passwords Encourage your
July 28, 2023
A significant rise in threats, mobility of our workforces and the internet of things has really changed how businesses operate. Just about every aspect of businesses today revolve around information technology. Even small businesses can no longer ignore the importance of having proper technology and security controls in place. If you’re like many businesses, you’re considering outsourcing to a company that offers managed IT support. Not only does this reduce costs, but it can also minimize headaches and your office space needs. But how do you know the managed IT support
July 14, 2023
Organizations heavily rely on technology to drive their operations, store critical data, and ensure seamless business continuity. However, the unfortunate reality is that disasters, whether natural or man-made, can strike at any time. That’s where a well-structured Disaster Recovery Plan (DRP) becomes indispensable. DRPs are comprehensive strategies and procedures designed to minimize downtime, restore operations, and safeguard data in the event of a disaster. Read on to learn more about the three essential components that should be included in every effective disaster recovery plan: Recovery Point Objectives (RPO), Recovery Time
June 27, 2023
The AME Group is named to the Bob Scott’s Top 100 ERP VARs for 2023. Organizations specializing in the sale and implementation of Enterprise Resource Planning (ERP) and accounting software are evaluated for the Top 100 ERP list. “We want to congratulate this year’s class of Bob Scott’s Top 100 VARs,” said Bob Scott, executive editor of ERP Global Insights (formerly known as Bob Scott’s Insights). “This selection represents recognition of leaders in this important field.” As the technology editor for Accounting Today, the publication editor of Accounting Technology, and
May 12, 2023
As the world of business continues to evolve, so does the need for small businesses to protect themselves from cyber threats. Cyber security is becoming increasingly important for all businesses, regardless of size, as the potential losses associated with a data breach or malicious attack can be devastating. Read on to learn why cyber security is so important for small businesses and the measures they can take to protect their valuable data. They Are More Vulnerable Compared to larger businesses, small businesses may have weaker cyber security protocols, which puts
April 17, 2023
As a construction company, you rely heavily on technology to manage your projects, communicate with clients and stakeholders, and keep your business running smoothly. That’s why managed IT services can be an invaluable investment for your company. In this blog, we’ll explore why your construction company needs managed IT services by looking at the benefits it can provide. Improved Data Security Construction companies deal with sensitive information such as project plans, budgets, and client data. Managed IT services can help you protect your company’s data from unauthorized access, theft, or
April 04, 2023
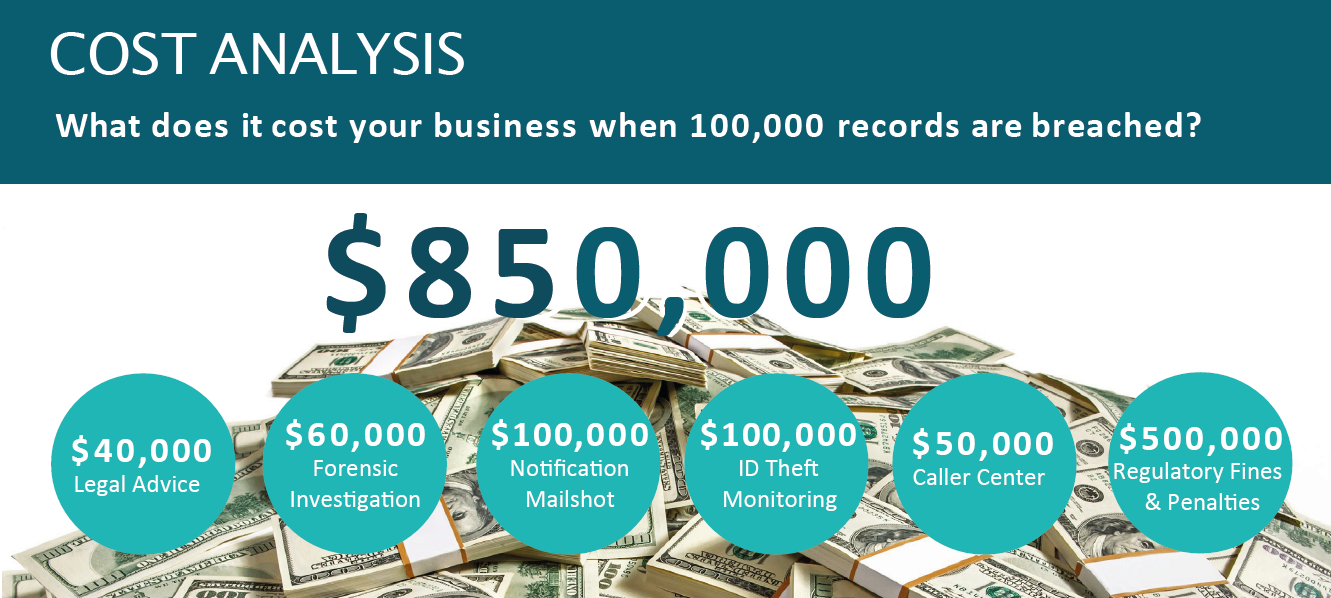
Data breaches are a nightmare for organizations because they lead to severe consequences such as loss of customer trust, legal penalties, and even business closure in some cases. Unfortunately, data breaches have become quite common in recent years as cybercriminals continuously find new ways to exploit vulnerabilities in systems and networks. For over 12 years, the United States has been ranked by IBM as having the highest cost for a data breach at $5.09 million more than the global average. Let’s take a look at the top causes of data
March 08, 2023
Having a solid business continuity plan in place will ensure that your company is better protected fromfuture emergencies or disasters. It can help reduce downtime, minimize financial losses, protectcritical business data and processes, and ultimately help sustain your business. Let’s review how toestablish such a plan 1. Identify All Potential Risks The first step to building a successful business continuity plan is to identify and assess the types ofrisks your business may face. These can include anything from natural disasters like floods or fires tocybercrime, technical malfunctions, supply chain disruption,
March 08, 2023
According to IBM, there are two main components of IT infrastructure: hardware and software. Manypeople don’t know the difference between hardware and software. Infrastructure is an importantcomponent of organizing your hardware and software. Infrastructure as a service helps companiesprovide you with efficient organization tools to improve your workflow. So, what’s the differencebetween hardware and software, and are they both necessary? Hardware vs Software The biggest misconception between hardware and software is that they are the same thing, with thenames being synonyms for each other. However, this is not the case.
March 08, 2023
Cloud computing is changing the world. It’s already changing the way we store our data, the way weplay our games, and numerous other aspects of daily life. The IT industry has also undergonesignificant changes thanks to advancements in cloud computing. Aspects of information technology,including data security, storage, and accessibility, have benefited greatly from the emergence of thecloud.IT services are quickly adapting to the cloud. We are the beneficiaries of that. Find out more about thedifferent ways cloud computing is changing information technology by continuing with the rest of thisarticle. Cloud
March 02, 2023
Phil Miller, Regional Manager from the Lexington, KY office of The AME Group provides consultation to many businesses looking to improve their business IT infrastructure. The point when business owners realize they need new technology or better management of their IT infrastructure, is where managed IT services providers like The AME Group can make an impact. We asked Phil, why do businesses need more than one IT person? If a company only has an “IT Guy,” it’s common that they face limitations in terms of their IT capabilities. As the
December 12, 2022
Most businesses, regardless of size or industry, are gradually turning to cloud services. They have realized they can benefit in many ways by making the switch. What helps is that cloud-based digital infrastructure is growing. According to Zippia, about 67% of enterprise infrastructure relies on cloud computing. With that said, some businesses are yet to embrace this technology as they don’t understand the benefits. The article below highlights some of the advantages of using cloud-based IT infrastructure. Enhanced Data Security One of the benefits of using cloud storage is improved
November 14, 2022
Business owners should be thinking about disaster recovery for work continuity. Every business owner should have reliable backups for their business. A DRP (disaster recovery plan) should be in place for your business. Learn what a DRP is and how you can formulate one. What is a DRP? A DRP for your business is a well-structured, written plan that outlines how your business will start working again after a disaster. It is a part of your business continuity plan. It will include reliable backups, how you will restart work, and
November 08, 2022
Do you find budgeting for IT challenging? If so, you aren’t alone. Here’s some tips to simplify your budget. While the IT budgeting process can be tricky for small businesses, it can be especially difficult for those trying to do it all by themselves. With so many aspects to consider, it can be tough to prioritize each and everything and still have funds left over for other crucial matters. One solution is to partner with an IT service provider like us. We can help you budget for all your IT
November 01, 2022
Do you have an IT Budget? If so, congratulations! You’re ensuring the success of your business. Budgeting for technology can be tricky. Threats persist and evolve as fast as technology changes. Avoid the most common budgeting mistakes to get the most bang for your buck! Here’s a list of the most common technology budgeting mistakes. Mistake #1: The cheapest option is always the best Your business technology shouldn’t be an afterthought. Investing in high-quality technology can significantly improve your bottom line. Excellent Reasons to Invest in High-Quality Technology 1️⃣ Streamlining
October 26, 2022
Give yourself plenty of time to review your IT budget to ensure your business has the resources it needs to continue to grow and prosper in the coming year. Business now know technology cannot be an afterthought. You need to have a clear and well-defined Strategic Business IT Roadmap to reduce unanticipated technology issues that could cause trouble. IT BUDGET: Assess, Document and Plan As technology advances at a fast pace, routine technology refreshes become increasingly essential for any company hoping to stay successful. Rather than simply assuming you’ll need
October 18, 2022
The answer is YES, there are often “blind spots” in your business insurance policies. Due to the high incidence of ransomware attacks last year, insurance premiums have increased as much as 40% and polices may have limitations to further protect the insurer. Mind the Gaps in Your Insurance Policy Recently, our Strategic Advisor in Evansville, IN gave us a few tips to better understand insurance policies. You should ask the following questions about your business’ Cyber Liability Insurance policy. Does my insurance coverage have sublimits? A sublimit is the maximum
October 13, 2022
First, you must train yourself to spot the signs of a phishing email. Second, you must practice. Then, you can protect yourself and your company. STOP and ask yourself, am I expecting this email? When you are in a rush or on a phone email app, STOP and ask yourself, can this wait until later to check more closely? If it doesn’t seem quite right, or expected, question it. If it appears to be from a co-worker, don’t reply, call them to verify any requests. Phishing emails can look just
October 11, 2022
Ransomware is a major problem for companies around the globe. Did you know businesses lose about $8,500 per hour because of ransomware-induced downtime, according to Comparitech? The CISA reports that, even though agencies and governments remain vigilant to uphold data security, malicious actors continue to reinvent their ransomware tactics. According to KPMG, the Covid- 19 pandemic opened doors to a surge in ransomware as cyber criminals targeted the less fortified computer systems belonging to people working remotely. For a ransomware attack to be successful, it first needs to gain access
October 05, 2022
Today, nearly every adult and child has at least one password. Most have nearly 100! The statistics around password management are rather grim. The most commonly strategy is writing them down in a notebook (31%). Remembering passwords is also a popular technique reported by 26% of the participants. (NCA). The most startling stat is only 45% of adults would change a password after a breach. (Google). The reason is it is hard for people to create and manage their passwords using only their memory. It’s time to change your strategy
September 28, 2022
First select a Password Manager – this blog shares some options. This example is using 1Password, but it’s a very similar process with all of them. It will show you the basics of how to use any password manager. You will need to download the application for your phone and your computer. You will also need to download it for all the browsers you use. It may be easiest to setup the account on a computer. You will start with a login username and password. Create a strong password by
September 07, 2022
MSP Verify Program offers vendor agnostic certification for Cloud and Managed Services Practitioners Worldwide; Provides Quality Assurance, and Stamp of Reliability for Current, Potential Customers The AME Group today announced that it has successfully completed the MSPAlliance’s MSP Verify Program (MSPCV) certification and SOC 2 Type 2. The MSPCV is based on the 10 control objectives of the Unified Certification Standard for Cloud & MSPs (UCS) and is the oldest certification program for cloud computing and managed services providers. The AME Group’s SOC 2 Type 2 audit was based on
September 07, 2022
Have you been surfing through a website or emails and had a message calling you to reveal personal information such as credit card numbers or passwords? You may have been subject to phishing. Phishing is an attack in which scammers pretend to be legitimate websites to collect personal information. Cybercriminals also use phishing to deliver malware to users. The following four tips will help you avoid such security threats. How to Spot a Phishing Message If you are to protect yourself from phishing, the first step would be learning how
August 26, 2022
In 2021, America experienced an unprecedented increase in cyber attacks and malicious cyber activity. Business Email Compromise is the most frequent attack vector. The FBI received nearly 20,000 complaints in 2021 that cost US businesses 2.4 billion. The second most costly digital crime type, investment scams, tallied about $1.5 billion in estimated losses. Your email account is an important part of your communication with employees, customers, and vendors. It’s often the everyday information that opens your business to attack, like who approves purchases, what applications you use, how you communicate
August 16, 2022
The number of businesses adopting online or digital services keeps growing yearly because of the many benefits they gain. That said, the transition to digital service forms comes with the risk of data breaches and network security threats. In cases where data thieves are successful, businesses often have to pay ransom to reacquire it or risk starting from scratch. According to PurpleSec, a 2019 study showed that 34% of businesses hit with malware took a week or more to regain access to their data. For businesses looking to better protect
July 06, 2022
As of September 1, 2022, five Microsoft 365 nonprofit licenses will increase. This occurs 6-month after commercial license increase to allow transition time from on-prem to cloud in a cloud-first program announced last year. This is the first significant price increase for Microsoft in over a decade. Since the initial release of Office 365 in 2011, Microsoft added 24 new apps and more than 1,400 features like Teams, encryption and automation. The price increase will impact nonprofit customers across all licensing channels (ex. volume, CSP and web direct) and billing
June 30, 2022
With the business world heavily reliant on digitalization in this day and age, the use of technology in your organization is unavoidable. Although technology can undeniably give your business an advantage in increasingly competitive markets, there are many troublesome areas to keep an eye on. This is why interest in cybersecurity has risen in recent years. Password protection is the best place to start if you want to ramp up your cybersecurity. Setting a password to secure an entity’s data is called password protection. Only those with passwords can access
June 24, 2022
Cyber security is a top priority for small businesses in 2022, and they must implement security measures that allow them to continue their normal operations even during an attack. According to PurpleSec, the risks associated with cyber-attacks are increasing as ransomware-induced downtime costs businesses approximately $8,500 per hour. Establish Threat Identification Routine One way to keep cyber attacks at bay is by establishing a process for identifying threats and taking action when necessary. This process involves setting up regular meetings with employees handling sensitive information, such as customer data or
June 21, 2022
What is Business Email Compromise? In a Business Email Compromise is also know as a BEC scam, or email account compromise (EAC). It’s when criminals send an email message that appears to come from a known source making a legitimate request. Every week this month we’ve assisted a business with a breach caused by stolen email credentials. It is by far the most lucrative attack for cybercriminals. Businesses need to start taking cybersecurity more seriously, as one government agency is warning that ignorance of best practices can lead to “catastrophic
June 15, 2022
There’s a long list of compliance requirements for businesses. PCI and HIPAA compliance are long-standing regulations that have driven credit card acceptance and healthcare entities for decades. Some that have tried to improve the security posture of impacted businesses, like CMMC with manufacturers, but have struggled to gain implementation and adoption. So, what is the strongest driver of compliance for your business today? Insurance and Supply Chain. Insurers are Driving Compliance Cyber Liability Insurance has been around quite a while, but due to the significant increase in breach incidents, they
June 13, 2022
If you think that your cyber insurance claim will be cleared with no questions asked, think again. Insurance claim denial has risen. While reviewing your claim, your cyber insurance provider will assess whether you took “due care” to protect your business from being compromised by a cyberattack. While having a cyber liability insurance policy is non-negotiable today, you cannot be fully assured that your insurer will cover any of the costs you incur following a security breach. Hidden in the fine print of your cyber insurance policy document are certain
June 09, 2022
It reminds us of the time(s) home owner insurers dropped residents of Florida after multiple hurricanes. Insurance companies are trying to stay afloat after a huge increase in claims. The soaring cost of breach incidents are changing the way insurers do business. As a result, it’s changing the way YOU do business. Insurers are requiring more from businesses before offering them cyber liability insurance coverage. And the cost of cyber liability insurance is increasing dramatically. The Soaring Cost of Cyber Liability Insurance Have you tried to renew your cyber liability
June 07, 2022
The COVID-19 pandemic has impacted everyone in one way or another. If there is one category that most benefited from the pandemic, it’s cybercrime. Cybercrime shot up by almost 300% since the start of the pandemic! Businesses are much more likely to be closed by cybercrime than fires and natural disasters. So, adopt measures to protect your business like having Cyber Liability #Insurance (CLI). Cyber Liability Insurance (CLI) covers the financial loss that results from cyber events such as data breaches. However, cyber liability is not typically included within general
June 02, 2022
in a cyberattack situation it is advisable to have a contingency plan that includes tech support for small businesses.
May 31, 2022
The technological landscape has advanced dramatically over the last couple of decades and continues to move faster than anyone could have ever imagined. Failure to keep up with the latest technology trends and current business practices can put your company at risk, but just investing in next-generation technologies does not guarantee successful implementation. When implementing new technology, you may want to get started as soon as possible so that you can reap the benefits right away. However, implementing new technology and solutions too quickly without following any change management best
May 26, 2022
It can be exciting to introduce new technology into your business. Finding a solution that will help your team members do their jobs more efficiently and effectively by filling a gap in your technology infrastructure is certainly an achievement. However, before you get carried away with quickly implementing technology changes, there are a few things you should know. Change Management Series: Part 3/4LINK TO PART 4 When introducing new technology into your IT infrastructure, keep in mind that change can be difficult for individuals. It can be hard to predict
May 20, 2022
Technology is advancing at an unprecedented pace, empowering businesses to accomplish more in less time. The transformations that technology has brought about in the business world are mind-boggling and with transformative change comes stress. The impact of ineffective change management can destroy business process and lose valuable people. Change Management Series: Part 2/4LINK TO PART 3 Without a defined change management strategy in place, avoidable inconsistencies are more likely to occur and you risk disrupting essential operations and losing valuable team members due to burnout. Keeping that in mind, before
May 16, 2022
Change produces stress in technology environments and among those who implement or are affected by the change. This is why change management is so critical for successful implementation. Once you’ve completed a technology audit and prioritized the order in which you’ll close gaps in your infrastructure, it’s critical to remember that there are actions you must take prior to implementation for change to be successful and well-received by your team. Change Management Series: Part 1/4LINK TO PART 2 Change management is an approach that deals with the change or transformation
May 11, 2022
The AME Groups ranks among the world’s Top 100 Vertical Market MSPs for their focus in healthcare (http://www.channelE2E.com/top100) for 2022, according to ChannelE2E, a CyberRisk Alliance resource. The annual list and research (hashtag: #MSP100) identify and honor the top 100 managed services providers (MSPs) in healthcare, legal, government, financial services, manufacturing, and additional vertical markets. Moreover, the research affirms that vertical market MSPs have vastly expanded their managed security capabilities. View the List Top 100 Vertical Market MSPs List 2022 Key Trends This year’s research revealed several key MSP business,
May 06, 2022
Outdated IT infrastructure such as computers, operating systems, and networks cause you to spend more time fixing security and efficiency issues instead of growing your business. Therefore, you may THINK you are saving money, but in the long-run you are not. By not upgrading your computer network, you are more likely to experience:➖ lower productivity➖ frequent downtime➖ lost data➖ lost customers➖ higher employee turnover➖ lost revenue | higher costsYou also open the door to cyber-criminals. With slower processing of information and a higher likelihood of a security breach, outdated IT
May 05, 2022
When talking about security threats that can affect a business, this no longer applies to physical threats, such as getting your inventory stolen by an intruder. Today, businesses also have to protect themselves against hackers and data breaches. Let’s consider the top things that businesses can do to protect against security threats. Train Employees to Recognize Phishing Scams Each year, businesses lose so much money globally to phishing scams. Simply put, phishing is when hackers use deceptive means and trick people into disclosing sensitive information or data. For instance, your
April 12, 2022
One of the many challenges you probably face as a business owner is dealing with the vague regulatory requirements present in HIPAA and PCI-DSS legislation. Due to the unclear regulatory messaging, “assuming” rather than “knowing” can land your organization in hot water with regulators. The Health and Human Services (HSS) Office for Civil Rights receives over 1,000 complaints and notifications of HIPAA violations every year.* When it comes to PCI-DSS, close to 70% of businesses are non-compliant.* While you might assume it’s okay if your business does not comply with
April 08, 2022
Why do small and mid-sized businesses (SMBs) need a compliance program? ✅ First, the trends are alarming. 42% of small businesses experienced a cyberattack in the last year. 75% was caused by giving too much privileged access to third parties. ✅ The free market is driving the demand to prove your business is secure, not regulations alone. You cannot buy cyber liability insurance without proof of your business security. You can’t receive an insurance claim payout without proof of your business security. Your supply chain and business associates demand it
March 30, 2022
While some people might only think data protection applies to large organizations, it’s essential for small businesses, as well. Small businesses are often targeted by security threats to steal sensitive data, making data protection a must-have for any sized organization. Here are some reasons why data security is important for a small business. Reliance on Online Platforms With the increasing reliance on the cloud and online transactions, many organizations are handling more and more data. Hackers will try to target this data for their own gain. The number of security
March 04, 2022
Currently, cloud storage is one of the most efficient options for storing data. By 2025, there will be more than 100 zettabytes of data stored online. There are a lot of providers who are offering this service, so you will never run out of options. With cloud storage, instead of storing data on-site on local storage devices, the data is continuously synced to a remote location. This data can be easily accessed using an internet connection. Here are some of the benefits of cloud storage for your business. Data is
February 16, 2022
The New IT intuitively responds to the universal realities of doing business. It equips you with solutions that keep yuo a step ahead in achieving these desired outcomes. Workforce Productivity and Collaboration Maximize uptime in the hybrid workforce reality. Infrastructure Flexibility and Agility Transforming enterprise computing to optimize business outcomes. Sustainability Improvements Cleaner, leaner operations with a smaller carbon footprint. Industry-specific Outcomes Customized solutions for specific vertical markets. Easy to implement solutions. Backed by world class support. Maximize your time and resources. The New IT Revolutionize Business New IT is
February 07, 2022
With technology ever-changing and with the latest updates on hardware and software, many businesses find it important to outsource their IT services. But this is difficult for most businesses because IT firms appear to be the same out there. In 2018, 72% of IT support firms provided disaster recovery services. If outsourcing IT services is an idea that your company has considered, you should then be aware of choosing the right firm that will meet the expectations of your business. To help you make the best decision, here are the
January 27, 2022
We kicked off 2021 with the Top 5 Business Technology Needs. They were Security Services, Cloud Services, Managed IT Support, Business Resiliency, and Business Productivity. In 2021, the challenges of 2020 not only remained, but grew. Now, we see there’s no going back to the way it was before the pandemic. This year, Business Resiliency and Security remain top IT Trends for businesses. The digital transformation continues. And the increased impact on finances by staffing challenges, supply chain disruption and inflation add stress to the business overall. As a leading
January 19, 2022
One of the many challenges you probably face as a business owner is dealing with the vague requirements present in HIPAA and PCI-DSS legislation. Due to the unclear regulatory messaging, “assuming” rather than “knowing” can land your organization in hot water with regulators. Are you taking a risk? Do you know if you are non-compliant? The Health and Human Services (HSS) Office for Civil Rights receives over 1,000 complaints and notifications of HIPAA violations every year.1 When it comes to PCI-DSS, close to 70% of businesses are non-compliant.2 While you
January 12, 2022
By adopting a Compliance First strategy, you will identify vendors and solutions that do not comply with your requirements. Then, you can eliminate them from your selection process, and select from the rest. It also means evaluating your current solutions and vendors and replacing those that cannot support your compliance requirements. In simple terms, compliance is anything someone else makes you do. This means laws, regulations, contracts, and even the terms of a cyber insurance policy. Failure to act responsibly can have devastating results. Your business could endure hefty penalties,
January 11, 2022
The internet provides everyone with access to constant information. While this creates convenience, it also opens you and your company up to threats, including attacks on data and personal information. When you do not have proper security in place, it leaves your business at risk. Common Network Security Threats Often security measures for a company become relaxed after some time, especially when there has been no sign of network security threats. However, once you have been the subject of an attack, you quickly remember how important security is. When 1,100
January 05, 2022
When you run a business, compliance and security are two essential factors. Both are equally important for the seamless operation of your business. While compliance helps your business stay within the limits of industry or government regulations, security protects the integrity of your business and sensitive data. It is worth noting that although security is a prime component of compliance, compliance does not equal security. This is because compliance does not consider the growing threat landscape and associated risks. What it considers, however, is a set of pre-defined policies, procedures,
January 04, 2022
Having a well-documented data security policy in place can help protect your employees, sensitive information and customers from security breaches. To develop a holistic policy, it is important to analyze all the areas that could be a potential threat. USE THIS CHECKLIST TO ENSURE YOUR DATA SECURITY POLICY INCLUDES ALL THE KEY ELEMENTS REQUIRED TO MAINTAIN DATA PRIVACY AND SECURITY DOWNLOAD THIS CHECKLIST AS PDF ✅SAFEGUARD DATA PRIVACY Apart from complying with the existing rules and regulations, a data privacy policy guides your employees on how to handle sensitive information
December 29, 2021
A compliance program aims at protecting an organization from risk. The purpose of corporate compliance programs is to ensure that a business complies with laws or regulations relevant to it. An essential element of an effective compliance program is a Business Impact Analysis (BIA). You could consider a Compliance Program to be a form of internal insurance policy to create evidence of conformity with regulations and instill a culture of compliance. Remember that establishing a foundation of compliance is a company’s best protection to minimize risk and increase business efficiencies.
December 08, 2021
Cloud storage refers to a cloud computing model that allows you to store data on the internet. The use of cloud storage by businesses has tremendously increased in the past few years, especially due to increased technological advancements, and is expected to continue growing in the coming years. With about 94% of all businesses using cloud services in different ways, cloud computing is more likely to stay and grow bigger in the future. You’re missing a lot if your business is not using cloud storage. The following are five reasons
November 30, 2021
Microsoft has launched a new Operating System (OS). Windows 11 has requirements that include hardware security features. There is a good chance that over 30% of your employee devices DO NOT meet the minimum hardware standards for this new OS. Likewise, third party tools and applications may also require updates or upgrades to operate under Windows 11. Ultimately, moving to Windows 11 could present hardware, software, and project costs to your business. What is AME Service doing about Windows 11? Due to functionality concerns, AME Service recommends an assessment to
November 29, 2021
Microsoft announced their first significant increase in price for Microsoft 365 Business and Office 365 Cloud Services in over a decade. Microsoft notes the continuous innovation and growth of these products are driving the increase. Innovations in communication, collaboration, security, compliance, automation and artificial intelligence are needed to match new operating models of organizations. Presently, there are no price changes for Education and Consumer Products. The new pricing structure will go into effect on March 1, 2022. Microsoft services will increase in price as follows: PRODUCT Current PricePer User New
November 26, 2021
Businesses are reaching out weekly for help meeting the requirements to purchase cyber liability insurance. The AME Group recently hosted webinars with guests from the insurance industry who confirmed the reason for this change. They saw a handful of pre-requisite questionnaires in 2020, but now they get several every month. The length of the questionnaire has grown and now insurance carriers also want proof of your answers. Why the change in cyber insurance requirements? It’s a simple answer – $$$$$. Cybercrime has grown into a profitable business model. More security
November 15, 2021
Remote working is on the rise. The benefits to both employers and employees are undeniable: it reduces gas consumption, makes for more productive employees, and provides a better work/life balance. But, as with any new technology or innovation in business practice, there are security risks that come into play when you start moving away from the office. Here are some strategies for protecting remote workers from security threats while still reaping all the benefits of remote working. 1. Communicate Security Policies and Procedures to All Employees Your IT department should
October 27, 2021
The New Workplace The year 2020 caused massive disruption, uncertainty and profound shifts at every level of business. As a result, we’re still figuring out what the new workplace looks and feels like. Through all this however, the pandemic has provided us with the biggest experiment in remote working in human history. In the midst of chaos, this year and last forced many to quickly adapt a remote workforce and how it’ll affect us in the short term, as well as shape our future. What will work be like in
October 21, 2021
Remember the first time your parents gave you a box of tools? I was moving out for the first time, and my dad gave me a box filled with an old hammer, two screwdrivers (one flathead, the other Phillips head), a rusty wrench, and a tape measure. It wasn’t much but it showed me that he wanted to make sure that I was ok. He gave me those tools so that I could fix any problems that came up in my time away from him. Well, we want to do
October 21, 2021
The AME Group collaborated with Evolve for a panel discussion on Cyber Liability Insurance for Manufacturing. Here what Jack Bowden with Evolve MGA says are the reasons manufacturers need cyber insurance. EXTORTION Your security is only as strong as the training of your employees. All it takes is one employee clicking on what appears to be an innocent link, but it’s actually malware. In seconds, your data is encrypted. Next, a hacker will contact you asking for a ransom ranging from a few thousand dollars to millions to decrypt the
October 13, 2021
October is Cybersecurity Awareness Month, but its also well known, among the vernacular of the younger generation, as Spooky Season. Most people are more concerned with ghosts, ghouls, and goblins than they are with the dangers lurking in the dark corners of the Internet. Which is understandable, it’s more fun to think about the fake monsters than the real ones who could change your life in an instant. So, let’s make a compromise. We’re going to list the 7 scariest ghosts and monsters when it comes to cybersecurity, and we’ll
October 12, 2021
Every business looks forward to protecting its data, as it helps determine the growth of the enterprise. However, you must invest in robust cybersecurity systems to realize better data integrity and privacy. The first step to realizing this would be to understand how to develop the right cyber security policy. Here are a few insights into how to create this cyber security policy for your business. Know Your Cyber Threat Landscape You’ll first need to understand the cyber threats and attacks your organization is likely to face. These problems could
October 07, 2021
If you’ve watched any sci-fi movie, you probably understand the perceived dangers of the digital world. Primarily the unrealistic dangers of artificial intelligence. Now, I’m not saying that AI won’t be a threat in the future but it’s important to note that right now the most dangerous threat is people using the Internet. They pose a much bigger threat than an incoming Robo-Apocalypse. And I’m not just talking about cybercriminals. Regular, everyday human error is what poses the most dangerous threat to your company’s cybersecurity. Don’t believe me? Well then,
September 28, 2021
Have you ever wondered where all those weird holidays come from? Like, who got to decide that April 23rd was National Talk Like Shakespeare Day? Or that Squirrel Appreciation Day would fall on January 21st? Or that the last Friday of every April would be National Hairball Awareness Day? An entire day to make sure that your feline friends aren’t spewing wet clumps of hair on to the floor seems like a waste of time, but do you know what isn’t? An entire month dedicated to cybersecurity. Now that’s a
September 22, 2021
Fifth-Annual List Honors Leading MSSP, MDR and SOCaaS Cybersecurity Companies Worldwide September 16, 2021: MSSP Alert, published by After Nines Inc., has named The AME Group to the Top 250 MSSPs (Managed Security Service Provider) list for 2021 (http://www.msspalert.com/top250). The list and research identify and honor the top MSSPs, managed detection and response (MDR) and Security Operations Center as a Service (SOCaaS) providers worldwide. The rankings are based on MSSP Alert’s 2021 readership survey combined with the digital media site’s global editorial coverage of managed security services providers. The fifth-annual
September 21, 2021
Deep Learning is a type of artificial intelligence. The goal of AI is to mimic the human brain. When you read more about a topic you learn more about that subject. Usually, that means you can make better logic-based decisions and predictions about that subject. However, as we all know, there is a limit to the amount, speed and complexity of the information we humans can process. AI engines can process information at a much higher volume and faster rate than humans. The prediction is that as quantum computing becomes
September 20, 2021
Your ERP system is at the heart of your business and nobody looks forward to a heart transplant. Yet, if the system is not supporting the needs of the business, limits your flexibility or inhibits customer service, a replacement is called for.ERP system replacement is a major business decision, and a major commitment of time and resources, so there has to be good reason to even consider it. So, how do you know when it’s the right time to change to a new ERP system? Your system does not support
September 17, 2021
Let Us Tackle Your Tech, So You Can Focus on Your Business You have a lot to juggle. Everyone looks to you for answers, instruction, and direction. It’s hard to carve out time in your schedule for what YOU want to do and for growth strategy implementation.Every business leader faces time constraints. It can feel like you’re a rubber band stretched to the breaking point.So, maybe you’re thinking about tasks to delegate to free time for you to work ON your business instead of IN your business. Our team of
September 09, 2021
There are a lot of network security issues that companies have to deal with daily. Some of these issues will go unresolved for long periods of time. However, this increases the risk of attackers gaining access to sensitive company material. Here are some common network security problems and how to fix them. Unknown Assets on the Network A lot of businesses don’t have an inventory of all of the IT assets that are linked to their networks. This is a serious issue. If you are not aware of how many
August 31, 2021
Is Your IT Provider Secure? On July 2, 2021, roughly 50 IT managed service providers (MSPs) were part of a cyberattack via one of the remote monitoring and management tools they used. While this not the software that The AME Group uses, it does serve as a wakeup call to both providers and their clients. You trust them with your business, but how secure is your IT provider? As with any IT managed service provider, The AME Group utilizes a collection of tools to help keep our clients efficiently running
August 20, 2021
The AME Security Team presents to our company related news and updates. This week features an internal story about how we come together to improve our existing security controls. It is challenging to keep up with the steady stream of news about security breaches and threats. Like many companies, The AME Group has teams across locations and working remotely. We connect via Microsoft Teams and work collaboratively most often in digital and virtual forms. This past week, the President of AME saw an article on LinkedIn. He sent it via
August 19, 2021
We don’t live in a utopia. Disasters happen. That’s why business owners take measures such as buying insurance to minimize the effects of disasters. While an insurance policy can protect your business against numerous disasters, it won’t protect it against data loss. That’s why whether your business is large or small, it needs a disaster recovery plan to safeguard data. That said, here are six key reasons why your business needs a disaster recovery plan: 1. Security Threats While you may take various internal measures to protect your business’s data,
August 11, 2021
It is more important than ever to choose an experienced managed IT services provider. Because technology has become more complex and critical to your business, it demands expertise, and verification by third-party audit. We perform various IT and security audits for our clients. Some audits improve the functionality, productivity and investment of their technology. Other audits assist businesses in achieving regulatory compliance and optimal cybersecurity. The health of your technology and security is as important as your financial health. Would you hesitate to perform third-party financial audits? Businesses lose millions
July 08, 2021
Technology has become an indispensable part of most business operations. It continues to bridge the gap between small enterprises and large corporations by leveling the playing field. Executives can now increase productivity, improve their customer interactions, and propel their revenue growth through streamlined marketing tools. New business technology solutions are coming up each year that can give your small enterprise an edge in the market. Here are five key IT solutions that you should have and how they can transform your business. 1. Migration to Cloud Storage The ‘Data Age
July 02, 2021
MSP Verify Program offers vendor agnostic certification for Cloud and Managed Services Practitioners Worldwide; Provides Quality Assurance, and Stamp of Reliability for Current, Potential Customers July 2, 2021 – The AME Group today announced that it has successfully completed the MSPAlliance’s MSP Verify Program (MSPCV) certification and SOC 2. The MSPCV is based on the 10 control objectives of the Unified Certification Standard for Cloud & MSPs (UCS) and is the oldest certification program for cloud computing and managed services providers. The AME Group’s SOC 2 audit was based on
May 27, 2021
After the pandemic, most organizations have been using virtual tools for different aspects of their operations. Most SMEs will need support and business technology solutions to streamline their projects. Here are some tools entrepreneurs may require to remain efficient and competitive. 1. Tools for Collaboration and Teamwork When it comes to technical support for businesses, one of the essential tools facilitates collaboration. Teamwork is amongst the most sought-after soft skills in the 21st-century workplace. There has been an increase in the utilization of teleconferencing software applications like Skype and Zoom.
May 05, 2021
N-Able launches their Super Elite program to better support top MSP performers. The AME Group is one of approximately 200 MSP partners to earn the distinction. This new designation distinguishes The AME Group as an MSP leader in the global IT channel. To select MSP Super Elite members, N-able carefully evaluated thousands of its MSP partners worldwide on a range of criteria. They included: a company’s overall size and service model; its consecutive growth and profitability; the number of IT devices proactively being managed using RMM; the productivity of a
May 03, 2021
Businesses across the globe are becoming increasingly reliant on technology to run their operations. Consequently, there is a growing need for quick, effective IT support. You can opt to hire and run an in-house IT team or outsource managed IT services. Outsourcing IT security and services allows you to focus on your core competencies without a worry about data management or IT infrastructure. However, before you opt for tech support for small businesses, you may need to take into account several critical considerations. To facilitate a smooth integration between your
April 30, 2021
In January 2020, the Defense Federal Acquisition Regulation Supplement (DFARS) formally added the Cybersecurity Maturity Model Certification (CMMC). The decision sent over 300,000 members of the defense industrial base (DIB) into a state of frenzy. Most of the members are small to midsize businesses (SMBs). Many found themselves drowning in all the unnecessary noise surrounding CMMC and its larger implications on existing and future government contracts. The chaos increased when the Interim DFARS Rule (DFARS Case 2019-D041) joined the foray on November 30, 2020. This rule mandates all defense contractors
April 27, 2021
Not much affects a company’s ability to serve its customers, compete effectively, and maintain long-term business growth like enterprise resource planning (ERP) system selection and implementation. This makes it, therefore, a high-risk proposition. When it comes to selecting or replacing an ERP system, you have to get it right or your company will pay the price – for years to come. It’s been said that replacing an ERP system is like performing open heart surgery on a patient while the patient is not only awake, but also on the job.
April 20, 2021
Our security analyst recently shared this at our Lexington Team Huddle, which makes for a good information to know if you want to create a strong PIN code. This content is from a blog post by DataGenetics. If you love statics, you must read the entire post, PIN number analysis (datagenetics.com); it’s fantastic. We create PINs to lock our phone, to get money out of an ATM, to get into our computers, to enter websites, etc. The length of many PINs are only 4 digits, which means there’s 10,000 possible
April 15, 2021
Right off the bat, we’re here to tell you that anyone promising you a sure-shot solution to all your CMMC woes is trying to pull a fast one on you. The Cybersecurity Maturity Model Certification (CMMC) is a comprehensive move by the U.S. Department of Defense (DoD) and involves a lot of moving parts that have not been finalized yet. In fact, with the planned rollout of the new CMMC requirements scheduled to take place over the next five years (through to 2026), you should expect a few changes or
April 13, 2021
5 Stats that Prove Identity Management Needs to be a Bigger Priority Infographic for Identity Management Day, April 13, 2021 from NCSA and IDSA. The AME Group is proud to be a #IDMgmtDay Champion!
March 25, 2021
Even prior to the pandemic, the increase in technological developments had already led to many business practices being handled remotely. Since COVID-19, remote employment has further increased, as it provides a way for companies to continue business as usual while still complying with social distancing guidelines. Although working remotely offers safety from the coronavirus, it places companies at higher risk of contracting computer viruses. As such, there are several network security threats for remote workers that your business should take into consideration. Phishing Schemes 45% of remote workers say they
March 22, 2021
Acumatica provides the best business management solution for digitally resilient companies. Built for mobile and telework scenarios and easily integrated with the collaboration tools of your choice, this leading cloud ERP software delivers flexibility, efficiency, and continuity of operations to growing small and midmarket organizations Join us on April 9th at 11 am ET to learn how Acumatica software can help grow your business. Speak with our Strategic Advisor, Gary Maystead, and see a demo of the core features. Webinar Agenda: Introduction to Acumatica Digital Transformation Core Products & Editions
March 16, 2021
Business owners need to be careful about network security threats in this day and age. A single network security threat can potentially bring down a whole small business, and unfortunately, this happens more often than you might think. This is because not only do many companies fail to hire technical support for businesses in the first place; but furthermore, many of them do not hire the right types of technical support consultants. Outsourcing IT is all well and good, but it’s important that the IT being outsourced by business owners
February 23, 2021
Throughout 2020, businesses and organizations faced many difficult challenges because of the “Work from Home” movement, increased cybersecurity threats, and ineffective communication with clients and employees. As a leading Managed Services Provider, we identified the TOP FIVE Business Technology needs of our clients. SECURITY SERVICES The first business technology need is securing and protecting corporate data continues to be the most pressing business need going into 2021. It continues to be challenging for businesses and security experts as they work to stay one step ahead of the criminals and threats.
January 27, 2021
By 2019, it was expected that the managed services market would hit $170 billion worldwide. These managed services particularly focus on technical support for businesses. Where business owners really want to focus in 2021 is cyber security. This is in part because more businesses have been pushed to rely on remote workforces in light of the pandemic, and have recognized that there will be benefits to keeping that remote workforce for the long term. A single lapse in cyber security policy could lead to a business’s integrity being permanently compromised.
January 06, 2021
Ideally, we have a health physical once a year. We assess what we are doing right, what we are doing wrong, and make modifications to our overall wellness plan as needed. Hopefully, nothing is wrong, and we can proceed with the usual cautions and goals of maintaining a long and productive life. The same could be said for our cyberhealth. How’s your Healthcare Cybersecurity Program? Did you make adjustments to meet the challegnes? This year, we not only had an unexpected curveball thrown at our businesses and networks, but we weren’t
December 24, 2020
Businesses today are more reliant on technology than they ever were before, and with good reason. Data can be stored for the long term without a need for printed copies and can be easily referenced by employees and business owners alike. In many ways, it’s much more difficult for businesses to operate without moving forward in terms of technological progressions. But there are risks that open up when businesses become reliant on technology, as unavoidable as this reliance may be. It can be difficult for employees who are not tech
December 07, 2020
There are many reasons why many major businesses have transitioned to different types of cloud computing. The cloud offers a great deal of flexibility for companies, allowing them to access programs remotely and maintain a great deal of storage. However, it’s not a foolproof system. Information can be corrupted, programs can crash, and perhaps most concerning, security threats can compromise crucial information. This is why it’s so important for business owners to consider outsourcing IT. When considering different IT service providers, business owners should look at the disaster recovery services
November 13, 2020
Join us today to get a clear picture of what Cybersecurity Maturity Model Certification (CMMC) means if you rely on DoD contracts to maintain your business. Joe Danaher, CISM, CRISC will answer questions and step you through what it means to your security program and budget to achieve CMMC Level 3: Good Cyber Hygiene. Get the latest updates from the DoD and clarify how the bar is being raised on cybersecurity for over 330,000 DoD subcontractors. The changes are necessary for the protection of America’s defense intelligence, but many companies
November 06, 2020
Are you a mid-market organization with multiple locations, multiple cloud services, and a complex network? If so, you would benefit from learning more about SD-WAN. In simple terms, what is SD-WAN? Software Defined Wide Area Network is a significant advancement in the technology of WANs. The key to SD-WAN is the centralized control using a software application (Software-Defined). Virtual networks are created on top of the hardware network. The main benefits our client seek are prioritizing their business application and better utilization of their internet connections. What Drives SD-WAN Adoption?
October 30, 2020
In this day and age, businesses have become increasingly dependent on the cloud. There are a number of benefits to working through the cloud. For one thing, it’s easier to maintain a system through digitization rather than keeping all important information in hard copies and paper documentation. Furthermore, it’s often much less expensive to operate through the cloud, which essentially allows employees to multitask and safely store their information. But then, as with any storage system, the cloud has its drawbacks. As the cloud has become more prevalent, hackers and
October 11, 2020
WHY SHOULD YOU BUILD A CULTURE OF SECURITY AWARENESS? The risks to all businesses due to cybersecurity breaches are well-documented and they are growing. Most experts advise businesses to plan for a breach due to the likelihood of an occurrence. Your IT staff have likely also been asking for additional resources to help combat the very real threats of bad actors that want to steal your data. As an owner or executive at your company, what is your role in all of this? The stakes are high and the threats
October 08, 2020
OCTOBER IS NATIONAL CYBERSECURITY AWARENESS MONTH #BECYBERSMART Top Tips from The National Cybersecurity Alliance. INTERNET OF THINGS Internet of Things (IoT) or smart devices refers to any object or device that is connected to the Internet. This rapidly expanding set of “things,” which can send and receive data, includes smartphones, cars, appliances, smartwatches, lighting, home assistants, home security, and more. #BeCyberSmart – connect with confidence and protect your interconnected world. WHY SHOULD WE CARE? Cars, appliances, wearables, lighting, healthcare, and home security all contain sensing devices that can talk to
October 06, 2020
We were was recently asked about the threat to privacy and businesses based on online behavioral tracking technology. While this has been around for many years, the sophistication of targeted advertising online has grown, yet, it is still not at a “Minority Report” level. The first step in understanding the threat is to understand the technology. Online behavioral tracking is a product of technologies built-in to web pages and web browsers that work silently in the background as you use the internet. Cookies and Online Behavioral Tracking Coding, called “cookies”,
October 04, 2020
VICTOR IS A SYSTEMS ENGINEER AT THE AME GROUP, MANAGING BACKUPS FOR OUR CLIENTS AND OUR OWN! WE ASKED HIM, WHAT IS IMPORTANT TO KNOW ABOUT BACKUPS AND RECOVERY? Backups are something everyone wishes they had when technology goes south. Like the insurance policy, you didn’t size right or bother to purchase. The need for backups AND reliable data recovery is becoming the number one priority for many businesses, and it should be. Even hard drive companies are starting to build data recovery services into their warranties and obviously at
October 03, 2020
Most everyone understands application software updates. We do it all the time with our phone apps, and most have seen a notification to update your computer operating system. They often give us new features, but, more importantly, they improve security. Software Updates / Patches Software updates are also known as “patches”. Think of them as patching holes in the software code to prevent cybercriminals from taking advantage of vulnerabilities and infiltrating your network. When software vendors find vulnerabilities (holes) in their software, they create new code to repair them. When
October 03, 2020
The AME Group joins vibrant global consortium of cloud, managed service providers and technology enabling vendors. October 3, 2020 — The AME Group announced that it has become a member of the oldest managed services group. MSPAlliance is the oldest Managed Services group and the only Accrediting and Standards based body created specifically for the Managed Services Industry. With thousands of members worldwide, the MSPAlliance is a very powerful and influential global network of IT professionals. MSPAlliance works in a collaborative effort with service providers, technology enabling vendors, governmental bodies
October 02, 2020
Outsourcing IT is a wise business choice, especially for the small business owner. But make the wrong choice and you just ramped up the security threat to your network. A lot of small business owners choose their outsourcing based on price alone, which can be a critical error. Network security threats are unlike physical security threats. There are literally threats around every corner in the cyber world. You have groups that are dedicated to hacking into networks and causing chaos as a pastime. Data security management for business has to
October 02, 2020
National Cybersecurity Awareness Month To reduce your risk of falling for a phishing scam, Think Before You Click! Start to look at emails from a new perspective Look at the email address Even if it is from a name you recognize, Think Before You Click! <somelongname8825@gmail.com> – Most business emails do not come from a GMAIL account – be suspicious. <info@amazonn.com> – Perhaps there is a spelling error that can easily be overlooked if rushing – be suspicious. TIP – on a phone email app, you don’t always see the
September 16, 2020
The AME Group Expands to Nashville, TN Nashville, TN – Richard Pinson, CEO of Advanced Network Solutions, a Nashville based Managed IT Service Provider announced today its sale to Advanced Micro-Electronics, Inc., DBA The AME Group (AME). Advanced Network Solutions (ANS) has been partnering with businesses in Tennessee and surrounding states providing technology business solutions for over twenty-three years. They will continue to do so under the leadership of The AME Group. Employees will continue their employment with AME in Nashville. Also, they have the opportunity to help support other
September 08, 2020
This is a timeless concept from roman times, passed down in popular culture, and can be applied to your business information systems security plan. Companies of even modest size and complexity rely on some form of IT to support their computer systems and data. Although, most companies trust their IT department or Managed Services Provider to include security as a baseline component of their work, how do you verify your IT security is dong what you THINK it is doing? A Risk Assessment is a valuable tool. Trust but verify.
September 02, 2020
Remote workers threaten 1 in 3 businesses Here are some tips to promote safe remote working. All of these are equally important. Make sure you understand best practices. Now more than ever it’s important for you to stay up to date on cybersecurity. If your organization has an ongoing training program, make sure you’re actively participating. Scams like phishing only INCREASE when employees are working remotely – you must stay in the know on current threats and best practices. Make sure you understand your organization’s policies and procedures. If you’re working remotely,
September 01, 2020
Technology in business today continues to impact the world profoundly. It has played a big part in the tremendous growth in trade and commerce we are currently experiencing. Modernization of IT infrastructure generates innovative solutions that allow small enterprises to tap into their full potential. From Infrastructure as a Service, high-speed internet to cloud technologies, the future is bright for companies willing to adopt the change. Here are some benefits of technology solutions for business. 1. Improved Business Agility Technology solutions allow small businesses to remain agile and quick to
July 30, 2020
Small business owners have enough to manage without worrying about tech support for their business. However, the benefits of investing in tech support for small businesses far outweigh the cons. In this post we’ll cover just a few of the main reasons why outsourcing your IT needs can help your business stay safe. Managing Business Security With so many dangers in the modern, technological world, the main benefit of tech support is to help you deal with network security problems that have the potential to threaten your business. Even a
June 26, 2020
Cybercrime is currently on the rise. In 2018 alone, cybercriminals stole over half a billion personal records through data breaches. With the threats evolving every single day, businesses are fighting to save face through enforcing effective cyber security policies. A cyber security policy creates an organizational framework that stipulates and coordinates a security program that combats the threats. Corporations, both large and small, need to hire data security management for business as part of their safety protocols. Check out seven characteristics of an effective cyber security policy. 1. Purposeful A
June 03, 2020
Many business owners overlook the importance of their IT department. However, implementation of technology solutions for business is essential to help a business’s overall wellbeing and growth. A high-quality outsourced IT department can help with network security problems, provide you with a trained staff and be cost-effective. Access to a Qualified and Experienced Staff While there are many businesses who may overlook IT altogether, there are others who spend a lot of time training their IT professionals. Worse yet, they may even hire inexperienced individuals to act as their IT
May 20, 2020
Sites are hacked every day. Your Information IS for sale on the DarkWeb. It travels quickly across the world and is viewed by thousands in a weeks’ time[1]. Once on the internet, whether on the surface internet (what we know of as the internet) or on the deep/dark web, you cannot erase it. Many evil things happen on the dark web, it’s not just about stolen credentials. Drugs are sold; people are sold; counterfeit money is sold; access to your server is sold. Your stolen PII / PHI can be
May 05, 2020
Cybersecurity Maturity Model Certification (CMMC) The CMMC started within the Department of Defense (DoD) to reduce the theft of military intelligence, but as expected, it doesn’t look like it will be long before it spreads to other sectors. There’s interest in amending Sarbanes-Oxley to include CMMC, which will impact the financial sector. Don’t fear this is just an additional burden – the CMMC model is set up to be clearer and easier to implement. Standardization in security compliance is a win for businesses trying to juggle multiple requirements. Impact of
May 01, 2020
In the digital age, we do almost everything online or with help from technology. We rely on our devices for both personal and professional use — and we think nothing of entering our personal information into web portals. But while technology can provide us with ample convenience, it can also increase our privacy risks. You might depend on accessing digital data at work, but criminals are after that access, too. In order to prevent security breaches and data loss, you’ll want to have a full understanding of the network security
May 01, 2020
We have more questions for Joe about the security concerns of working from home. To start with, how many AME employees are working from home, and what types of adjustments have you made from a technical/cybersecurity perspective? We have almost 200 AME employees working from home. Sixteen offices have a staff person present to receive shipments. AME was well-positioned with laptops and secure connectivity to all of our applications (including our phone system) we need to provide 90% of our services remotely. Our staff is fortunate to have home
April 21, 2020
The reality of working from home goes beyond business collaboration adjustments and the technical and workspace setup. The people who share your workspace also need to adjust to your new working arrangement. Suddenly working from home can inadvertently cause friction, aggravation, and even embarrassment during the workday. The best way to manage these situations is to get ahead of them and have an open, two-way conversation about needs and expectations. This is a sample conversation that can be adapted for your specific situation. While it might not directly apply to
April 16, 2020
STEP 1: Make sure to click on every link, and download every attachment sent to you via email. On mobile, feel free to trust links sent to you in random text messages. STEP 2: Disable antivirus and other security apps on every device, especially your work computer. STEP 3: Ignore security policies. They’re more like suggestions than hard guidelines anyway. STEP 4: Plug in that random USB flash drive you found. It could have some good information on it! STEP 5: Feel free to download sensitive information to a personal
April 14, 2020
As far as software is concerned, it’s safe to say that change is the new normal. Unfortunately, if there’s one thing people are bad at, it’s—you guessed it—change. You can have the best technology in the world, but if your users aren’t willing to change along with it, your investment may end up sitting on the shelf. THE UNMOTIVATED MAJORITY 80% of users are skeptical of new software and reluctant to change. Successfully rolling out software is one thing, but getting users to adopt their productivity tools percentage embracing
April 07, 2020
Are you Ready? 5 Things You Will Love About Moving to Microsoft Teams Email will always be important, but when it comes to modern collaboration between teams, there’s a better way! Microsoft Teams is a chat-based collaboration hub that’s built on the principles and best practices of the modern workplace. Here are five ways Microsoft Teams will help you and your teamwork smarter together. LESS BACK AND FORTH Teams is a workspace that saves you from the scatterbrained norm. The average user works (or tries to work) with 10 desktop
April 02, 2020
We offer a personalized approach to learning. Each user creates a profile to identify their experience with Microsoft applications and their job characteristics, such as travel, work locations, involvement in management, activities, and type of devices used. An individualized Skill Path makes it easy to access and complete training relevant to the user. Assigned courses with due dates and feedback on progress helps the user navigate their learning. Quick Long courses are difficult to add to your day and hard to take in. Course videos are “bite-sized” and QuickStart
April 02, 2020
If you’ve just started your small business, you’re probably running on a tight budget. Given that you are bootstrapping, you may not be able to pay for a full-time IT professional for your business’s IT support. However, to grow your business in the digital age, you need technical support. So what’s the best move to make? Managed IT is the go-to solution for thousands of small businesses in the United States. These small-to-mid-sized enterprises need IT support but may not be able to afford an in-house IT department quite
April 01, 2020
How people adapt to changing technology will define the future of their careers, their organizations, and the world. Embracing change is a no-brainer, but the workforce continues to fall behind. Here’s how to make change work with you, not against you. Love it or hate it, technology is everywhere. Technology powers us through our workdays, connects us to the world, entertains us in our off-hours, and helps us create additional technologies faster than ever before. We don’t just depend on technology; we live and die by it. But our relationship
March 23, 2020
If you’re not on a VPN, what steps do you need to take to protect your company when you are working from home? Your employees must use 2FA (Two Factor Authentication) to access business applications. We recommend 2FA whether you are in-office or remote, also use strong passwords, like passphrases that are greater than 10 characters in length. Make sure your workstation has current patches and updates for the OS (Operating System), Web Browser and Adobe PDF Reader. Also, it is vital to have Anti-virus (AV). Windows 10 comes with
March 23, 2020
You are busy running your business. The day-to-day management probably takes up all of your time and energy. However, businesses can be struck by adversity. How a business responds to these situations can make the difference between survival and a premature end. Here are three examples of policies that a business should develop before they are needed: Cyber Security Policy A cybersecurity policy has a few components. Hardening systems: A robust network use policy can help to limit how far hackers can get into your system. Moreover, managing user profiles
March 20, 2020
Our partner, Brainstorm, has put together a two-part series to help you and your staff be successful working from home using Microsoft Office 365. Working from home doesn’t have to mean business slows. Join us to learn the right tools and strategies so you can still be productive and collaborative outside of the office, using Microsoft Teams and other O365 tools you already have. If your staff needs online training on how to effectively use the Office 365 suite of apps for remote collaboration, learn more and request a
March 19, 2020
AME is working with many of our clients to establish Business Class remote connectivity solutions, but we know many of you may require something sooner to fill the gap. To help our clients whose COVID-19 response requires remote working capabilities, AME is extending the use of our Remote-Control Management Software to our managed desktop clients. This tool will allow home workers to securely connect to their office PC using their home internet and PC. This service should not be considered a replacement for VPN as the preferred method for employees
March 19, 2020
Regulatory compliance is an issue business has faced for years. Over time, not only have the regulations become more nuanced, they’ve become more difficult to track and address, as well. Given the importance of remaining compliant, it’s no wonder why businesses from all industries rely on The AME Group for assistance. The AME Group understands compliance requirements and has the tools to help you handle them with ease. HIPAA, PCI and GLBA are just the tip of the iceberg. Compliance regulations can be traced to global policy, national policy, and
March 12, 2020
Are you taking your IT security as seriously as you should? If not, the consequences to your business or organization could be devastating. A security breach could lead to lost data, stolen data, or other irreparable harm to your company’s reputation. You need to develop a security program. Don’t take chances with your IT security. Call in the experts at The AME Group. We specialize in all aspects of IT security. Of course, we will help you cover your basic needs, develop a security program, and help you in ways
March 05, 2020
If you’re a business owner, you know how important perception and professionalism can be to your brand. With it, you can do business with anyone anywhere; however, without it, you’ll struggle to attract the customers you need. The AME Group understands the importance of professional-grade business email and has experience managing it. With an equal understanding of security and efficiency, The AME Group provides maximum business email benefits to its customers. Top-notch spam filtering helps minimize distractions and threats via your email. Heightened security eliminates lost time caused by unnecessary
March 03, 2020
Second, and requiring more of your attention is increasing compliance requirements. Your business is more likely to fall under compliance or be asked to prove your security before another company will do business with you. Many states passed laws on their own that differ from each other and this can be costly for businesses to be compliant and even understand how they need to be compliant. A national compliance standard is needed for businesses handling Sensitive Data. Follow your State Chamber as they are most likely lobbying for national guidelines
February 27, 2020
Chances are that your business relies on IT. Over the past two decades, nearly every industry has integrated technology solutions into the core of its daily operations. This makes IT security an increasingly important factor. One of the key questions a business faces is whether its IT is secure. The AME Group provides real answers by offering IT security audits that put your system to the test, identifying strengths and weaknesses so that you know where you really stand. No doubt, you have certain controls in place to secure your
February 25, 2020
Proactive Prevention & Protection It’s been proven that a comprehensive and continuous security education program can effectively reduce phishing click rates by up to 64%. With phishing being one of the top attack methods used by cybercriminals, investing in a phishing and education program has been shown to output a 37-fold Return on Investment. If a criminal does get through? That’s when one of our robust cyber insurance policies, covering up to $1M, comes in! Ponemon Institute. “The Cost of Phishing & Value of Employee Training.” Related Blogs
February 20, 2020
What do you know about your company’s information security policies? Do you have methods in place to maintain confidential data, availability of data, and integrity of data in the face of malicious Internet threats? Once you understand what a necessary part of your business strategy information security is, it’s comforting to know that you can partner with an industry-leading IT security company like The AME Group. The AME Group can help you and your staff understand everyone’s role in information security. Each employee must be educated about the various threats
February 12, 2020
WHY A SECURITY RISK ASSESSMENT MAKES SENSE Running a business has inherent risk factors. During the course of each month, you need to pay rent on facilities, pay employees for their time, and purchase supplies that you can translate into your own products and services. With a small business, there is a constant risk of not being able to meet these demands. That’s why it’s so important to limit risk wherever you can. The AME Group understands this and has services specifically tailored to reducing risk for customers (specifically IT
January 28, 2020
In 2018, a meager 72% of Information Technology (IT) companies offered disaster recovery services. More than ever before, businesses today have a lot of highly-sensitive cloud-stored data. Although some companies have on-premise servers, outsourcing IT services is more beneficial. One of the advantages is that outsourcing IT is cheaper. Moreover, outsourcing IT services means leaving the job to experts. The different types of cloud computing today do a good job in terms of data protection. Even so, such technology solutions for business can’t protect data that’s interacting with other systems.
January 07, 2020
Higher Education has seen some changes in Compliance Regulations causing these organizations to evaluate their security. Here’s a list of safeguards you must have in place. Gramm-Leach-Bliley Act (GLBA) applies to higher education institutions because they participate in certain types of financial activities that are defined in banking law. Administering federal student loans is one of the main activities that pull institutions under GLBA compliance regulations. However, because colleges and universities don’t entirely fit the traditional model of a financial institution, the FTC has provided some flexibility on the privacy
January 02, 2020
Did you know that, according to the University of Maryland, a cyber attack happens every 39 seconds? With more and more information being kept digitally, the threat to your own data is large if you do not take preventative measures. This is why the managed services market is projected to reach 170 billion U.S. dollars worldwide by the end of 2019. If you’ve been curious about what measure you can take to keep your information protected, or want to know how you can upgrade your current IT security measures, check
December 12, 2019
The National Education Technology Plan believes in providing students with greater access to IT support for schools. Funding digital learning is no longer a dream. It’s a reality to maintain the standard of education across the country. Let’s dive into the top reasons why IT support for schools is a necessity to see better learning results from all students. 1. IT Support For Schools Simplifies the Learning Experience The phenomenal growth in technology that has occurred over the past ten years attributes to higher test scores. This data is seen
December 02, 2019
Cloud computing refers to a technology that provides computing resources via the internet. The technology makes it possible for virtually anyone with an internet connection to take advantage of storage, processing, and software resources. Cloud computing providers make use of three broad, often overlapping, implementation models. This article begins by looking at the various cloud computing models. Understanding these models is what makes it possible to define the different types of cloud computing in the next section of the article. The main cloud computing implementation models are: Infrastructure as a
November 28, 2019
Here at The AME Group, we enjoy helping our clients throughout the year with all their IT needs. From security and cloud solutions to custom development, we have numerous ways to help businesses of all sizes. Now that it’s Thanksgiving, we’d like to pause to express our gratitude to everyone who entrusts their IT needs with us. 2019 has been an exciting year for our company, and we know it’s been an exciting business year for many of you, as well. Being granted the opportunity to help other people grow
November 01, 2019
Of all IT service providers, only 72% of them offered disaster recovery services in 2018. This is one of many important things to consider when you’re looking for customizable tech support for small businesses. This is doubly important if you’re the owner of a company. After all, any new business needs the best in tech support to get off the ground. Before you think about outsourcing IT responsibilities, here are some things you should know about tech support for small businesses. Getting Technology Solutions for Businesses Does your business need
October 25, 2019
LEXINGTON, KY – October 1, 2019 – Integrity IT, a Lexington based Information Technology Consulting company announced today its sale to Advanced Micro-Electronics, Inc., DBA The AME Group. Integrity IT has been partnering with Kentucky businesses to help them make the best use of technology for nearly 20 years now and will continue to do so under the leadership of the AME Group. Phil Miller, the former President of Integrity IT will continue as the General Manager of the Lexington Office and 2 other partners, Joe Danaher, CISO and Bryan
October 06, 2019
Network Abuse – DON’T PUSH YOUR ‘LUCK’ Look around your office. Isn’t it great to see your team hard at work on their computers? Yet if we take a closer look, let’s see what’s really happening… Joe, your new sales rep, is poring over last weekend’s game stats… Amy in marketing is looking for a new job, surfing your competitors’ websites, chatting with their HR people… Wes, over in customer support, just bogged down your entire network by downloading a video file of Metallica in concert… Guy, your new hire in shipping, is on
October 02, 2019
Technology solutions for business are riddled with acronyms and technical terms. Even those in information technology (or IT, our first acronym) would admit as much. But if you are an entrepreneur looking for tech support for small businesses you might get lost in the alphabet soup. Take cloud services, for example. There are many different types of cloud computing, including cloud storage, infrastructure as a service (or IaaS), platform as a service (or PaaS), and software as a service (or Saas). Many non-technology companies still make heavy use of technology.
September 15, 2019
2FA, or two-factor authentication is a form of MFA (Multifactor Authentication), that requires a second layer of security for your application and online access. Take advantage of this option and set it up wherever it is offered. Double-up your login protection. Many technology companies and app-makers provide two-factor authentication that requires users to authenticate their identity over two devices. This is becoming more the norm and is a great foil for anyone trying to access accounts unauthorized. The process is usually really easy to use, but just remember to keep
August 30, 2019
Regardless of how much time your company puts into service or product development, it’s virtually impossible to please all clients always. Your company will certainly have to address customer complaints and answer their questions at one time or another. You should thus ask yourself whether you will have the right answers for these customers when they call. It’s important to be prepared because they’ll need you to answer to their concerns so that they can make their repairs. Customer service needs more than just an FAQ section and the posting
July 29, 2019
Data security management for business is important to protect both your company and your clients. Whether you are storing medical and healthcare data or customer financial information, in today’s world no data is safe from unscrupulous individuals or organizations. At least, not without solid data security management, that is. Keep reading for more information on how you can beef up your cyber security and protect your most valuable asset – your data. Determine Network Security Threats Before creating and implementing a cyber security policy, it’s a good idea to determine
July 03, 2019
Information technology (IT) is a key part of all businesses these days. In some way all companies require data storage and technological support. However, not all IT companies are the same and it’s important to look for one that offers you the things your business needs. Outsourcing IT security and services can be a wise move for your business so long as you know what to look for when choosing a provider. Here are some factors to consider and some questions to ask when you’re looking to protect your business
June 04, 2019
For many businesses, cloud computing provides an affordable and scalable solution for data management and backup. Different types of cloud computing serve different purposes, but the vast array of services out there provide solutions for all kinds of businesses, no matter how simple or complex. Along with the convenience of easily being able to store data off-site comes a risk of attack by outside parties. This risk is infrequent, but you want to be prepared and have a plan in place in case an attack does happen. Currently, around 25%
May 10, 2019
It can happen in seconds. With one quick click of a mouse by an employee, a slight gap in security infrastructure, or a weak cyber security policy, a hacker can suddenly take down everything a business worked so hard to build and protect within their organization. The wreckage could include anything from shutting down company-wide internet access to stealing financial data. Even manufacturers of power distribution units are victims of cyber crime, as attackers can hack into the power cables running data servers. Although this may seem like something out
April 04, 2019
Cloud storage has become one of the best ways to save and store data for businesses throughout the country. Whether you’re running a large business or starting a small business for the first time, cloud computing offers the best in disaster recovery and easy access to all your important files. Here’s how cloud storage can change the life of your business in 2019. It’s easy to use Cloud storage enables all your important files to be saved in one location. This is essential when it comes to usability and accessibility,
March 15, 2019
Ask anyone: Cloud storage is the cutting edge of technology in the modern age. In fact, an estimated 2.11 billion people worldwide are currently using some form of Cloud storage, and that number is only projected to go up. If you’re one of those people, you probably want to use cloud computing for your business in the most efficient and effective way possible. There are a lot of different kinds of software out there that will help you with this, and it can become overwhelming and scary. Fear no more!
March 11, 2019
The AME Group will be partnering with Fortinet, the world’s leader in cybersecurity, to host a free lunch event at Topgolf Fishers on April 24th, 2019. This is the perfect opportunity to learn more about network security threats in 2019, while enjoying some complementary food and indoor golf. Space is very limited, so click here to register: We hope to see you there!
February 20, 2019
Did you know that 7 out of 10 consumers have admitted they would pay more money for a business with better customer service? Which explains why so many businesses are turning to escalation management to enhance their approach to customer care. If you’re looking to implement escalation management into your own customer service center, read on to learn the most effective ways to establish one. 1. Self-Service Makes Life Easier Your first line is allowing the customer to find the answer themselves. You may be surprised to find that many
February 19, 2019
Nearly every business relies on technology to operate efficiently and profitably. But as software and hardware become more complex, so does the threat landscape. Here are some of the ways you can stay one step ahead of the people trying to harm your business. Malware: What it is: Chances are, you’ve probably had a run-in with malware at some point. Short for “malicious software,” malware is a term used for any application or piece code designed to cause harm to or steal from a device within an organization. It is
January 16, 2019
99% of computers are vulnerable to exploit kits. Why? Because almost everybody has downloaded Adobe Reader, Adobe Flash or Java. This highlights one thing: networks are extremely difficult to secure against attack. One thing you can do is be aware. There are threats everywhere in life. But being aware of the right threats at the right time will help you prepare and fend off any attack. Today we’re going to talk about a few network security threats blooming in 2019. 1. Network Security Threats: Software Subversion When you can’t get
December 18, 2018
Your company’s most valuable information is probably stored somewhere on a server. Many people don’t fully realize that information is more valuable than money though, and so they secure it less. Yet, data security management for business in all industries is invaluable. If that information leaks the consequences can be worse than getting robbed. Customer information leaking to hackers can cost them their homes, finances, sanity, and safety. If hackers access your company’s information, you may even be sued for neglecting to handle that information carefully. Implementing data security can prevent
November 14, 2018
Up to three-fourths of all companies did not prepare for a cyber threat. And the threat of faulty cybersecurity continues to rise! Are you willing to let your company suffer next? It’s not hard to protect yourself, and well worth it to keep your files and integrity safe. Let us show you the many causes of network security problems and how you can fix it. Did You Mean: Network Security Problems It doesn’t take a lot of searching to find some of the most common network security issues. Here are the major ones.
October 21, 2018
No matter how “bomb-proof” we make your network, you and your employees can still invite a hacker in if you click on a link or open an attachment in an email sent by a cyber-criminal. Some spam is obvious (can you say, “Viagra at a discount”?) but others are VERY cleverly designed to sneak past all the filters and trick the recipient into opening the door. Known as a “phishing” email, this still is the #1 way hackers get around firewalls, filters, and antivirus. It is critical that you and your
October 12, 2018
TIP #1 – ENCRYPT ALL LAPTOPS We are not going to get into the details of data encryption and you don’t need to fully understand what data encryption is to understand the benefits. The HIPAA Security Rule states that if patient data is encrypted and the data is lost or stolen there is no need to notify patients or report the breach. The official description of encryption is that it is a Safe Harbor under the HIPAA Security Rule but we like to call it the “get out of jail
October 10, 2018
When you’re thinking about building a tech-savvy, productive business, cybersecurity needs to be at the forefront of the discussion. Create a culture in your company that focuses on the protection of your sensitive data. When you hire new employees, they definitely need to be up to date on these matters. If you’d like to build this sort of company culture from the ground up, follow the tips below. Implement Cybersecurity Training for New Employees When hiring new employees, we often think about filling out documents for HR, getting them acclimated
October 09, 2018
More and more businesses are undergoing a digital transformation. What does that mean? For many, it’s implementing multi-cloud solutions in an age of big data. If that sounds like a lot of buzzwords, let’s break it down. Businesses are choosing cloud solutions, but they aren’t without security risks. Meanwhile, it’s becoming popular to run a business on democratic, high-velocity data. All this makes way for new vulnerabilities. Compliance agencies seek to regulate risk. Here’s how IT regulatory compliance solutions may enhance your business: What Are IT Regulatory Compliance Solutions? Regulatory
October 02, 2018
At last count, the Small Business Administration estimates that almost 30 million registered small businesses exist today and many more operate under the radar. What that means for your small to medium-sized organization is that it’s extremely important to maintain a lean structure, optimize your processes, and invest your resources in things that will allow you to maximize your impact on the market. But how exactly does an organization go about doing that? One of the most popular methods for achieving that end, especially in today’s tech-focused age is to
September 25, 2018
You know you need tech support for your small business, but like most other business owners, you believe it’s too expensive for you to buy into. It definitely seems like a good thought, but when you look further into it you might actually be hurting yourself. Technical problems can pop up at any moment. If you aren’t prepared to handle them, they could sneak up on you and mess with your computers and other technical belongings – and by then, it’s too late. So now the question isn’t whether you
September 18, 2018
Many decision-makers at companies find themselves questioning the value of IT consulting companies. For a lot of them, it really comes down to a lack of knowledge of what consultants do. It doesn’t help that there are so many kinds of consultants, all with varying levels of expertise and value. Use this guide to learn the basics of IT consulting and how to determine if your business can benefit from it. What Are IT Consulting Companies? An IT consulting company works with clients to help them solve IT problems. The
August 31, 2018
What if you could have all the benefits of a more efficient company and none of the risk? We know that this sounds too good to be true. However, it can happen for your own company when you learn how to outsource the smart way. You’ve probably heard some horror stories about outsourcing gone wrong. But we’ve got good news: we put together a comprehensive guide to how you can beat the top risks of outsourcing! 1. High Costs Perhaps the most obvious risks of outsourcing are the added cost.
August 24, 2018
There just aren’t enough hours in the day, right? Well, that may be the case for most companies. But businesses who outsource their information technology work to IT consulting companies benefit from great service as well as a whole lot more valuable free time. Here are 10 things you and your team can do with your free time once you outsource your IT needs. 1. Focus on Business Growth Perhaps the best reason to outsource your IT needs is so that you and your team can focus on growing your
August 17, 2018
Not every company has the budget or capacity to hire somebody with IT expertise, but that doesn’t mean you can do without IT support entirely. With $100,000 lost on average every hour during an IT outage, you can’t afford to be without the support of IT professionals. So why do companies outsource their IT? Isn’t it safer and cheaper to hire internally? That’s what we’re here to answer. Here are 3 of the main reasons why businesses and organizations like yours decide to outsource their IT. Lower Costs and Risk
August 10, 2018
The global market for IT outsourcing is nearly $90 billion and levels of IT outsourcing are the highest that they have been in five years. With so much money being spent on outsourced IT services, it is obvious that it must be beneficial for businesses. Otherwise, they would be spending that money on in-house IT. But are there risks involved with IT outsourcing? And do the benefits outweigh the risks? We take a look at some of the biggest risks and why the rewards more than outweigh them. 1. Some
July 27, 2018
Automation of routine tasks has revolutionized jobs and the economy. Although automation is a huge threat to job availability, it certainly does make our lives easier. IT consulting companies are often at the forefront of automation, streamlining, and innovation. One trend that they employ is having a ticket system to keep track of HR matters and even invoicing. You may have seen the words “open ticket” and “pending,” but what do they mean? More importantly, what are the differences between them? Keep reading for four important differences between the two
July 20, 2018
Emails from businesses about compromised data are becoming common. Customers are also quick to voice their ire about downtime with their IT companies. System downtime alone can cost $26.5 billion in revenue every year. But outages don’t have to spell the end of your business. All you need is an IT disaster recovery plan. Not convinced? Read on to discover the 5 reasons why your business needs one. 1. Human Error is an Ever-Present Problem We entrust so much to our computers these days but we forget that it’s still
July 13, 2018
With so many risks to data security, businesses need to be on alert to ensure their policies and devices are compliant with legislation. The risks to your business are enormous, especially given that costs for compliance failure can run into the millions. But with so many compliance problems facing businesses today, how can any business be sure that they’ve got the right policies in place? To help out, here are 5 of the most common IT compliance issues facing organizations today. GDPR-Compliant Data Policies The EU’s General Data Protection Regulation
July 06, 2018
Big data and analytics is the process of examining large amounts of data from day-to-day production to improve business. Today, new technologies provide a unique insight into products, bringing big data in manufacturing to light. This new form of analytics is comprehensive and allows business owners to connect dots to enhance their processes across the board. Big data analytics is catching fire with over half of companies using its insight to drive sales and overall success. So, how can it improve processes? Let’s get into it! The Perks of Big
July 02, 2018
An increasing number of companies are employing IT managed services. It’s not hard to see why. The business world is becoming more and more reliant on information technology. So many companies are realizing that they can save on cost while staying ahead of the competition in IT developments. By employing managed IT services, companies can improve efficiency. This is because they are concentrating on the rest of the business. While they can leave the experts to take care of the IT services. Keep reading to discover the 5 reasons why
June 25, 2018
Have you ever been on your computer doing important work and suddenly see a pop up for a software update? Have you ever been so busy you decide to update later but never do? If you have been asking, “Why are software updates so important?” You are not alone. The fact is, software updates are very important and sometimes we don’t realize it until the software stops working or we lose important information. If you have been ignoring important updates, please continue reading because once you know all the facts,
June 18, 2018
In 2017, small to medium-sized businesses in North America spent nearly $300 billion on IT services. And as long ago as 2014, over 90% of small to medium-sized businesses in the US were using cloud-based business solutions. IT is playing a larger and larger role in the running of businesses of every size. And more and more of those businesses are turning to companies that can offer managed IT solutions. But what do you actually get for your money? What can you expect from your IT managed services provider? Learn
June 11, 2018
You might know by now that an IT department is a must for your business. Is your current IT support running smoothly? Maybe it’s working for now but, you might be in the process of scaling your business. If this is the case, you’ll need to invest a lot of money if you decide to keep all your IT staff members in-house. If you want a more efficient and cost-effective solution, outsourced IT support might be your best option. You might’ve heard about it but, aren’t sure how it will
June 06, 2018
VINCENNES, Indiana – June 1, 2018 – Advanced Microelectronics, Inc., DBA The AME Group, announced today it acquired the assets of Orion Group Software Engineers, a South Bend, IN-based Information Technology Consulting, Custom Software Development and ERP Software Solution company. “The team at Orion Group have done a tremendous job supporting their clients,” said Mark Gerkin, CEO of The AME Group. “They understand the needs of their clients by designing custom software solutions, implementing ERP solutions as well supporting their IT infrastructure, which is something we value. Combining the advantages
June 01, 2018
Cloud managed services provide comprehensive business IT solutions. Businesses prefer this option for their security and flexibility. Cloud managed service providers fill gaps in a businesses technical skill set shortcomings. There are several types of cloud-based services for business needs. This includes security & backup to computing & data management. Why outsource services vs keeping them in-house? Read and find out. Cloud Management Services: 10 Unbeatable Benefits You’ll want cloud services by this article’s end. Let’s explain why. 1. Lower IT Costs Businesses requiring IT services save money using third-party
May 25, 2018
Initially, when you’re starting to roll out an IT security and compliance program, it is important to get everybody involved. The way that you get everybody to buy in is to first of all understand, what is the endgame? What it means by that is what does it look like if your organization was to be hacked or was to be attacked? What does that mean to your customers, your profitability, and what does that mean to your job? Are you going to be there tomorrow if this company’s primary
May 21, 2018
…THEN YOU’RE PROBABLY A CYBER-CRIMINAL’S NO. 1 TARGET! In a world of rampant cybercrime, hackers thrive on the blind faith of their targets. Despite high-profile digital security breaches showing up in the news nearly every week, most people assume they’re safe from attack – TOO SMALL TO BE HACKED. The thinking goes that while Fortune 500 corporations like J.P. Morgan, Sony, Tesco Bank, and Target have lost millions of dollars of data breaches in recent years, my business is far too small to justify a hacker’s attention…right? Wrong. In fact, it’s quite
May 18, 2018
When you started your business, you probably didn’t bank on micromanaging every little aspect of it. From payroll to marketing, to IT, sometimes you can lose track on what’s important in your business when you’re caught in the weeds. You may have heard rumblings about managed service providers (MSP). But what is an MSP? Today, we have a complete guide for you on managed services and why they’re important to your business. What Is An MSP? The idea of MSPs really took off in the 1990s when they were called
May 15, 2018
The HIPAA compliance checklist is more extensive now than it was in the past. If you are working in the medical field or know someone who is, read here for the newest checklist to make sure you won’t end up with a large fine on your back. Who is Covered Under HIPAA Typically HIPAA laws affect any establishment who creates, maintains, or transmits PHI. Most healthcare providers employed by a hospital are not covered. The hospital itself is covered and must be held responsible for enforcing HIPAA compliance laws. Employers,
May 11, 2018
At this point, the average data breach costs businesses around $3.6 million dollars in lost future revenue, your damaged reputation, and lawsuits. This kind of loss is a major hit for even the most stable business. To avoid these kinds, of issues, you need to know the biggest IT compliance problems and how to solve them. To ensure IT compliance, you need proper training. You need to not only explain what needs to be done but why it’s important. Putting into place checks and balances will ensure everyone complies. Here
May 08, 2018
Every 39 seconds there is a cyber attack affecting one in three Americans every year. With such a drastic increase in the number and complexity of cyber attacks, naturally, the cyber protection industry is having to keep up. The Department for Digital, Culture, Media and Sport (DCMS) in London is planning to set up a ?13.5m cyber security innovation center. With more insight, money and manpower geared towards the cyber security movement, more exciting advances and innovations are being made. Here are five trends that are taking the cyber security
May 01, 2018
Every business, no matter how large or small, depends on technology to get through the day. Because of our increasing reliance on technology, the demand for information technology (IT) specialists has dramatically risen over the past decade. A great IT professional can keep your business safe, online, and well-functioning. But if you’re looking to hire some experts, you have a very important decision to make. Should you outsource IT or hire in-house? Here are the unique advantages and disadvantages to both to help you make a more well-informed decision. Outsource
April 24, 2018
It’s difficult for businesses to manage their own IT services if they don’t have the bandwidth, staff, or expertise. Hiring a company, or a Managed Service Provider, helps with important IT needs. Without it, your company is losing precious time and money, while decreasing productivity and focus. Read this article to learn why managed IT services are so important and how they help your business be successful. What Are Managed IT Services? Managed IT is a great service provided that combines unlimited and flat-rate support into a monthly payment. The
April 10, 2018
Over 75% of small business owners claim they don’t have a disaster recovery plan in place. This statistic is quite alarming, especially when you consider the thousands of cyber-attacks on businesses each year. Many studies have determined that almost 40% of businesses that experience a cyber-attack close their doors soon after. Instead of waiting until disaster strikes, now is the time to work on developing a business continuity and disaster recovery plan. Working with IT professionals is the best way to hone in on what this plan needs to succeed.
April 03, 2018
Why is small business such a big deal? According to the Small Business Administration, more than 99 percent of American enterprises fall into the “small” category. That’s a good reason! If your company falls into the mix, be sure you’re opting for the best cloud storage you can get. All it takes is one power outage or technology failure to find yourself in a rough patch. The good news? With the best cloud storage partner on your side, you don’t have to lose sleep. Below are five ways to ensure
March 27, 2018
Many people mistakenly believe that HIPAA violations are made by medical providers alone. In some cases, however, American school systems are required to comply with HIPAA. Each year, there are thousands of HIPAA violations investigated by the United States Department of Health and Human Services (HHS). The penalty for a HIPAA violation is up to $50,000, with a maximum fine of $1.5 million for multiple violations. The vast majority of these violations occur at a hospital or doctor’s office. In rare instances, a school can violate HIPAA laws as well.
March 21, 2018
When your website is slow, down, or has its security compromised, you’re not only losing serious profits. You’re also losing consumer trust. If it’s been a while since you’ve evaluated your current network, chances are, there are probably already lots of issues that you’re not even aware of. You could be leaving customers’ sensitive information vulnerable, or you could be dropping in search engine rankings because of poor site and network performance. Is it time for a network assessment? Read on to find out when is. 1. You’ve Already Been
March 20, 2018
Losses due to cybercrime in the U.S. continue to grow, exceeding $1.3 billion in 2016. Cybercriminals work from around the world in the borderless world of cyberspace. Increasingly, organized crime groups are responsible for these activities. All this means that cybercrime represents a serious threat to businesses around the globe. Your business needs to protect your IT systems and valuable sensitive information. We’re going to tell you about the cybersecurity statistics you need to pay attention to. 7 Key Cybersecurity Statistics You Should Know 1. Cost of Cybercrime Damage Increasing
March 14, 2018
Every business knows that having highly trained and skilled IT professionals on board is essential to their operations. Businesses today face a grave danger of a security breach due to viruses, hacking and other threats. There are 1.5 million cyber attacks every year, and the majority of them are aimed at businesses. But it’s hard to find good IT employees. The job market for IT professionals is highly competitive and salaries run high. Searching for a good IT manager using recruiters, employment agencies or ads doesn’t guarantee you’ll find the
March 07, 2018
Are you always on top of backups and security when it comes to your business? If the answer is yes, you’re half-way there. Now it’s time you learn about business continuity solutions and what they can do for your business. Remember you can never be too careful. Read on to learn more. What Is Business Continuity? Business continuity refers to your company’s ability to remain functional during or after a disaster has occurred. Regardless of the size, all businesses can benefit from a business continuity plan. The first step to
February 28, 2018
Despite the extent to which our society now relies on technology, many healthcare facilities are still struggling to transition to a digital recordkeeping system. Old habits die hard, so there are a couple of reasons for this resistance. For one, some healthcare providers fear that technology solutions will not be user-friendly. Others are concerned that technology will present security concerns for their patients. But are paper records really the right choice for healthcare providers? Let’s take a closer look at how a digital recordkeeping system could provide a better option.
February 14, 2018
While browsing the internet, you may have come across a term that sounds straight out of a sci-fi novel — machine learning. So what is machine learning, and when does the robot takeover begin? There’s no reason to panic yet. Machine learning is a pretty tame application of the concept of artificial intelligence, so humans should be safe for now. What this groundbreaking technology actually means for us is a new and more powerful way to analyze data. Read on for an overview of how machine learning works. What Is
February 07, 2018
Businesses invested between $26 billion and $39 billion on artificial intelligence in 2016, which is triple what was spent in 2013. Not bad considering AI is still in its infancy. There’s a reason why AI in the workplace is continuing to become more and more popular. Businesses can use this technology to improve efficiency and productivity. This frees up employee time to work on more important tasks. Here are 4 reasons why you should consider using artificial intelligence in your workplace: 1. Chatbots When people have a question or concern
January 31, 2018
The internet and technology have quickly become our primary means of communication. In fact, recent surveys show that 87% of all Americans use the internet. For this reason, many businesses have begun to take advantage of various technology tools like websites, online videos, and mobile apps to connect with customers. No matter what kind of internet tools you use, their successful operation relies on Application Program Interface (API). APIs are programming instructions that allow users to interact with web tools. To give your customers a consistent experience, API monitoring technology
January 27, 2018
There have been a lot of interesting developments in Password Management since NIST, National Institute of Standards and Technology (a division of US Dept. of Commerce), revised the 14-year-old guidelines last November with final updates issued in June 2017. The now-retired 72-year-old author of the original 2003 NIST, Bill Burr, was quoted in The Wall Street Journal as saying “Much of what I did I now regret.” Great Britain’s National Cyber Security Centre has also chimed in with similar updated recommendations on Password Security. Many of the recommendations are targeted to IT system administrators regarding steps they should be taking.
January 24, 2018
We all know that we need to make strong passwords to protect our data. That’s easier said than done. By now, you’re probably aware of the popular techniques to protect your password. You can add numbers or special characters to your password. You can also change your password frequently. These tips may have worked in the past. However, hackers are becoming more adept at hacking passwords than ever before. 40 percent of people have had their information compromised, account hacked, or password stolen. Are you looking to make your password
January 16, 2018
IT teams face a lot of challenges keeping business systems in operation. Dealing with compliance can get in the way of that progress. But without the right compliance solutions, your business itself is at risk. The number one goal of your enterprise is to drive business value. There are countless human and technological assets that go into its development. It’s easy to overlook the necessity of compliance. But compliance has become as innovative as any other branch of IT. New technologies streamline compliance management for large companies. This is true
November 30, 2017
IT has been one of the most emerging fields. Since technology is constantly revolutionizing, there are new IT developments that change. Changes in IT are necessary, but understanding them and how they will affect the future of technology can be difficult. There is no better way to practice innovation than in the world of IT, so we are constantly faced with new IT trends. Technology has a mind of its own, but it takes a great IT specialist to understand these trends. To better prepare for the future, here are
November 22, 2017
Running a business requires a large amount of time and resources. One of the key responsibilities of the business owner is to manage all of his or her employees. But, if you are able to outsource that work for a cheaper cost, then the smartest business decision is to do so. Infrastructure outsourcing is a common business practice. In 2016 alone, US business owners outsourced approximately 1,457,000 jobs. This not only increases efficiency but also frees up time and money for the company. In the past, only larger, more successful
November 21, 2017
Does updating your business technology sound like an over-complicated headache? New hardware and software integration isn’t as complicated as you think! Let’s put it into context: You started out as a small business, but have grown into a larger enterprise. Now you’re looking to streamline everyday processes with new technologies. This is far more common than you think! In fact, it’s rated in the top five biggest tech concerns for many small-medium businesses. Let’s break down simple ways to tackle hardware and software integration for your business. Approaching Hardware And
November 15, 2017
The National Education Technology Plan believes in providing students with greater access to IT support for schools. Funding digital learning is no longer a dream. It’s a reality to maintain the standard of education across the country. Let’s dive into the top reasons why IT support for schools is a necessity to see better learning results from all students. 1. IT Support For Schools Simplifies the Learning Experience The phenomenal growth in technology that has occurred over the past ten years attributes to higher test scores. This data is seen
November 14, 2017
Since almost 85 percent of small businesses have fewer than 20 employees, capacity can be a huge challenge. The firm’s few employees are often stretched thin, and take on multiple responsibilities outside of their regular job description. This is why many small businesses end up managing their technology with an impromptu IT team. Rather than hiring a dedicated specialist, the business relies on the most tech-savvy employee to manage their systems. While this strategy can be effective, it is important to get an outside review in the form of a
November 08, 2017
Sometimes it helps to have your head in the clouds. Cloud computing in healthcare is on the rise. 83% of healthcare providers are using cloud computing. That number is increasing each year. The cloud has opened many new doors in healthcare which lower costs and create better care. Here’s how cloud computing is revolutionizing the medical sector. The Importance Of Cloud Computing In Healthcare Quick Access To Information In healthcare, time is a valuable resource. A few precious seconds could save a life. Information stored in the cloud is quickly
November 07, 2017
Technology unfurls at an incredible rate. Not even ten years ago, there was no such thing as a smartphone. Mobile technologies have revolutionized the world of work and the world in general. A more current technology is cloud computing, which promised to be the next big wave of progress. How about artificial intelligence cloud computing? The two technologies are in use together. There are more advancements predicted for the near future. Right now, AI only accounts for 1% of the global cloud computing market. But its share of the IT
November 01, 2017
If you’re looking into getting the most from your company, the best thing you can do is get your IT compliance under control. When you let your IT issues get out of hand, you’ll run the risk of security threats, downtime, and other issues that create a rift in your business. As the CIO of a company, it’s crucial that you do everything you can to get a handle on your compliance needs. But what sort of compliance issues should you pay attention to? Read on and learn all about
October 31, 2017
These days, it seems like there’s data theft around every corner, doesn’t it? You hear so much about all of these big companies getting hit with data breaches and theft, it gets a little scary. If the big guys are getting hit, what can a little guy do? It’s not as hard as you might think to protect yourself. While there are many places a breach can occur, email is often one that people don’t stop to think about. Here’s how you can protect yourself and your data from email
October 16, 2017
Most businesses view their website as one of their biggest assets, and while it certainly can be, it can also be the biggest vulnerability. All the hard work your company does to generate traffic and promote itself online can go up in flames if you’re not protected from network security threats. Network security risks are so troublesome because you may not be aware of an issue until the damage has been done. If you haven’t already, you need to start protecting your company’s network now. Below, we’re discussing some of the most
October 09, 2017
Successful companies must have a comprehensive enterprise strategy. An enterprise strategy is your business’s approach reaching targeted customers and carving out a profitable niche in the market. These days, technology is crucial to this strategy. In fact, more than half of all workers report to using two or more devices at work. When using so many devices, it’s important to be able to seamlessly access data on each platform. To accomplish this, many businesses invest in a cloud computing system like IAAS to backup data. While there are several data storage options,
October 02, 2017
Employees at a small business or start-up are required to multi-task. They’re trying to build a customer base while also growing a business model. It’s demanding work, and sometimes things can slip through the cracks. . After a long day, there are few resources and little time left to dedicate to IT. However, you shouldn’t just let this work fall by the wayside. Instead, you should implement a smart IT strategy — which starts with an IT audit. Outsourcing your IT needs to the experts is cost-effective. Starting with an audit is a
September 25, 2017
Today, many businesses use their cyber infrastructure to run some of their primary operational processes. With cyber threats and hacking on the rise, companies are also investing in better security systems. In fact, the worldwide cybersecurity spending is forecast to hit $1 trillion by 2021. No matter how strong you think your current cyber security plan is, the reality is that all businesses have the potential to be attacked. In today’s world, breaches and cyber attacks are the new normal. As such, you need to be always prepared with a cybersecurity
August 30, 2017
With the wide use and availability of the Internet comes convenience. But the Internet also brings all sorts of threats. If your company is like most, you have an endless amount of business data. Did you know that there is a 1 in 4 chance of your company being the victim of a data breach? Did you know that the average data breach costs more than $3 million? Preventing data breaches and other network security threats is all about hardened network protection. Without proper security protocols, your business data is
August 17, 2017
The average data security breach takes less time to pull off than it does to prepare a cup of coffee. In fact, 93% of successful data breaches occur in less than one minute. Yet, 80% of businesses take weeks to realize a breach occurred. There are many costly consequences of compromised data. This is why 86% of business executives believe cyber security threats, such as weak data security, are concerning. Here’s a quick look at 5 of the most significant ramifications of data breaches. Keep reading to find out why it’s crucial to keep your business’
August 14, 2017
In today’s digital world, any business that wants to remain competitive must rely on strong IT support. If you’re planning your IT infrastructure, you may be tempted to think that maintaining an in-house IT department for all technical support and services is the way to go. However, the advantages of outsourcing can be considerable. This is especially true if you are running a start-up, or a mid-sized company seeking to grow. Let’s examine the pros and cons of outsourcing below. But, let’s see why you would ever consider in-house IT
August 01, 2017
When you’re running your business, you’re focused on your customers, your level of service, and your profit margin. Meeting government-mandated IT regulations may be the furthest thing from your mind. But ignoring these regulations can be a costly mistake. According to IBM, the average cost of a data breach is $3.62 million. Compliance management can help your business stay ahead of issues before they become major problems. What Is Compliance Management? Compliance means making sure your company meets your industry’s rules, regulations, and obligations. In the IT world, compliance usually
July 25, 2017
Every successful business in today’s day and age has a division that is largely technology based. No matter what product you sell, you likely have a sales or marketing team that attempts to reach out to customers through the internet. That’s why IT support for business is absolutely essential. Something will definitely go wrong at some point, that’s just the nature of technology. Nothing is perfect. Do you have the expertise to make substantial repairs to your network if something goes haywire? Even if you do, you are busy running your
July 18, 2017
The cloud has transformed the way businesses and consumers interact with the Internet, data storage and even software. That’s a trend that doesn’t look to be changing anytime soon. Over 90% of businesses already use the cloud in some capacity. Before delving into the nitty-gritty of cloud computing advantages and disadvantages, it’s helpful to remember that cloud computing isn’t just one thing. At present, it includes three distinct areas: IaaS – Infrastructure as a service PaaS – Platform as a service SaaS – Software as a service Even though the
July 11, 2017
Every few months, there is another breaking news story about a massive data breach. Sometimes it seems like no organization or corporation is safe. Last year, Yahoo confirmed a data breach of roughly 500 million user accounts. Even the United States government security clearance system was susceptible to a cyber-attack. Two years ago, hackers obtained Personally Identifiable Information (PII) of nearly 22 million federal employees and contractors. Major international corporations like Home Depot, Target, and Sony have all been the victim of massive data breaches. In this hazardous cyber environment, data
June 30, 2017
Imagine you’re working on a really big project when all of a sudden your computer crashes. All of your hard work is lost. This is a major problem, especially when there are deadlines to meet. Unfortunately, many businesses don’t take this seriously. 96% of all business workstations aren’t being backed. That’s a large amount of potential work being lost forever. Businesses are slowly starting to see the importance of having backup systems. This includes using cloud storage services. More than 50% of surveyed IT professionals have ranked backup and disaster
June 28, 2017
Nowadays, it is hard for your business to succeed if you do not embrace technology. This is because technology is becoming part and parcel of efficient business operations. With the increased use of more technology, there will come that time when you need to seek assistance from an IT professional company. Below are some of the signs that your business needs helps from a managed IT services provider. 1. Increased operation costs There is that time that you might find that your overall business costs are going high. At such
June 25, 2017
The recent Amazon data breach news has intrigued many businesses, especially small and medium enterprises (SMEs) to assess their own exposure towards data breach. As a small business owner, you are likely to think: “if such a big business as Amazon is exposed to data breach, how about mine?” Although this thought can pressure any business owner or manager, it is important to know that there are signs that one can identify indicating that your company data could be at risk so that you are in a better position of
June 22, 2017
What’s ahead for IT outsourcing in the latter half of 2017? The drastic change in 2016’s IT outsourcing trends introduced Cloud and enterprise systems (SaaS, PaaS, and Iaas). An increase in machine learning capabilities will continue to shape 2017. IT outsourcing trends no longer center around the need to do a task faster, better and cheaper. Instead, the necessity of achieving more strategic business outcomes is more important. To meet this goal, new skills need to rise in the market. Beyond this, a new American administration envelopes global outsourcing in uncertainty.
June 20, 2017
A lot of different things go into a running a business. If every department isn’t working in harmony together, you’re bound to run into problems. Imagine what would happen if the head of sales didn’t show up to an important meeting with a new potential client. Can you see your day going well if there was an employee conflict and HR was unreachable? People are important to offices, but the systems they use are even more crucial. IT services are important for every business regardless of their industry niche, and
June 19, 2017
For any businesses, utilizing a managed IT services provider offers a way to reduce costs and to increase the level of security on your organizational network at the same time. While you are going about the process of doing your everyday business, managed IT services provider is making certain that your network is safe from threats and, most importantly, the people who work at the security service provider are always up to date on the latest threats and able to provide you with solutions to deal with them as they
June 16, 2017
Is your company vulnerable to a data breach? If so, you’re letting your patients down. The more high-tech our world, the more vulnerable we are to data breaches, whether it’s accidental or malicious. That’s a sad truth that anyone in the healthcare industry needs to be aware of. This year alone, the UK’s NHS had their systems brought to a standstill by ransomware. So what healthcare data solutions can you use to protect your patients from data breaches? Updated hardware and software Modern data security is an ever-escalating arms race, and
June 16, 2017
One of the largest problems small businesses face is running their own IT services. Not only is it expensive, but it is also heavily time-consuming and takes time away from the business. This time would have been better used to focus on the business’s core functions. The best bet for a small to medium sized enterprise is to get a managed IT services provider. Luckily for most businesses there is a whole host of IT companies out there who’ve built an extensive line of software designed just for their needs.
June 08, 2017
It can be terrifying to discover that you have malware on your computer. This is especially true if you keep essential files like pictures, documents, spreadsheets, and videos stored on your hard drive. When you discover a critical error on your computer, you may panic and not understand what to do next. That’s exactly what IT support scammers are counting on — and they’re all too happy to “help.” In just the past two years, that bogus help has cost Americans a whopping $24.6 million, according to the FTC. So how
June 06, 2017
Are you a business owner considering ways to help you store data more efficiently? If so, you should look at the options available to your business through cloud computing. Cloud computing is when you use a network of remote servers online to store and process data. This allows you to access and manage data from those servers instead of on your personal computer or smaller, local server. Read on to learn more about the different types of cloud computing! Software as a Service (SaaS) Software as a service (SaaS) allows
May 18, 2017
There are a lot of companies today that simply do things on their own, hoping to save some cash in return. Is it really a good practice or something that should be changed? A lot of companies fail to fill the role of tech expert for different reasons. Lack of knowledge and lack of manpower are some of the most common reasons why companies fail to fill the tech gap on their own. Hiring a tech solutions company can be a great asset for your company for many reasons. Here are some
May 16, 2017
If you’re looking for short-term, specialized help with your business, then an IT consultant might be perfect for you! Who doesn’t want to save time and money when it comes to business? That’s the whole point of it right? Well, when it comes to needing IT assistance, often times hiring an outside source is the way to go. Outsiders bring a new perspective to your business plan, as well as expertise in the field and an objective, honest opinion. Often times businesses will pawn IT jobs off on an existing
May 09, 2017
School isn’t what it used to be. Chalkboards have been replaced with SMART boards. Pencil and paper have become Chromebooks and tablets. It’s only a matter of time before virtual reality education can be found in every classroom across the country. The benefits to this educational approach are endless. Virtual reality brings students to another world, another level of understanding, right inside the classroom. All students learn at a different pace and in different ways. Some are visual learners, others work best with hands on stimulation or verbal commands. Virtual reality education will
April 23, 2017
In an earlier time, you had to keep your pen drive or storage device with you to store your photos, music or other digital data. Thanks to cloud storage, now you can get almost all of your data at any place in the world easily. But every good thing has some drawbacks as well, as is the case for cloud computing as well. If you fail to use your cloud storage wisely, then you can create a security risk for your data in various ways. Here are 5 tips for cloud
April 20, 2017
Every single private company has critical data to protect, whether it’s monetary, staff or personal. Here are a few thoughts on how to progressively approach protecting that data. If you’re worried about keeping up your security, but you can’t survive without your group of gadgets, read on for 5 simple approaches to protect your data and your protection. 1. Security Updates Continuously guarantee that all basic security updates are introduced on your PC. These are discharged by Microsoft every month and settle known security issues that have been found. In
April 17, 2017
Can you imagine doing everything manually in your business? Technology can help companies perform better. But what makes technology appealing to companies? It is the possibility of cutting the manufacturing cost. And in the end, it makes the company more efficient and gives them the opportunity to save. Here are five ways technology can help lower the overall manufacturing costs for companies. Lessen mistakes and errors Manufacturing cost shouldn’t be just about the finished product. If the product is faulty, this will also be a liability to your company. You
April 14, 2017
These days, it isn’t enough that you have the best doctors, nurses, and health professionals to deliver the best healthcare. If a healthcare facility is using old methods, there is still a good probability they will make mistakes along the way. Also, it costs more for healthcare facilities to deliver the same level of healthcare than those organizations using new technologies. Today, healthcare facilities are adopting technology in order to improve services to patients. Here are six ways how technology can help improve patient satisfaction. 1. Lessen the workload of
April 11, 2017
Businesses have the responsibility to stay in touch with the latest technology. Integrating technology with your operations can make a huge impact on overall performance of the company. Computers, smartphones, and other technology are now used in order to improve or even expand an organization. Unfortunately, there are instances when business goals are not aligned with your technology integration. For some businesses, they simply fail to adapt these technologies. In these scenarios, businesses have no other option but to update their technology. Here are signs that your business goals are
April 08, 2017
Dropbox, Google Drive, and even the Google Chromebook laptops, are just some of the latest developments in the world of cloud computing technology. In reality, the use of a cloud is growing in popularity for many reasons. People are starting to use the cloud regularly these days even on their smartphones. And for businesses, utilizing cloud computing tech can make a huge difference. Here are some reasons why business, regardless of size should turn to this type of technology. Reduces the IT cost Many times, businesses are forced to spend
April 05, 2017
Data security is now in demand. It is one of the most sought after services in today’s IT industry. Regardless if you are dealing with security breaches or insiders accidentally or intentionally leaking data, these are just some of the most common problems that companies worry about. Before calling the help of a managed IT services provider, it is important to bust some myths that you usually encounter with data security. Myth 1: Information leak prevention is solely the security administrator’s responsibility If you will look at businesses today, the
February 26, 2017
Many managed IT service providers are finding it necessary to start offering 3D printing solutions. Though the technology isn’t brand new anymore, many businesses have yet to embrace this technology and without knowing are losing their competitive edge. It’s high past time to update your business technology! According to statistics, 71.1% of manufacturers have embraced 3D printing and 52% of manufacturers foresee the technology growing tremendously over the next 3 to 5 years. These statistics should have any company that has yet to invest in 3D printing worried. The following are some ways 3D printing will
February 23, 2017
Technology is causing massive changes in all sectors of the economy. These changes have been felt in the health sector, financial world, entertainment, and even government. The good news is that these changes will make the world a better place! One of the key sectors that has been affected by this disruption is education. These innovations are giving classrooms a new look and have changed the ways in which lessons are conducted. Here are the top six technology innovations that are causing major changes in education. 1. Virtual Reality (VR) in Education Virtual Reality
February 20, 2017
Technology has become an indispensable part of the business realm. Online marketing has become far more popular when compared to the traditional commercial system. The world is constantly going through a technological revolution. It is an extremely difficult task to keep up with the exponential advances in science and technology, but this is what separates the rapidly growing businesses from the stagnant businesses which have refused to acknowledge the importance of upgrading their technical infrastructure. Business owners must constantly relearn how new technologies affect their marketing, advertising, and servicing strategies so they can
February 17, 2017
There is a sense of insecurity when you think you are being stalked. Except in a case where you hire a bodyguard, no one likes to be followed around. This is what home network hackers do. They only difference between a stalker and a hacker is that stalkers cause physical harm and hackers cause virtual harm. This is why you need to know some IT regulatory compliance solutions. To prevent a hacker from gaining access to data stored on your home computer, there are four mistakes you need to avoid: 1. Using an
February 14, 2017
Technological changes have had a major impact in the business world. Advances in technology have enabled businesses to communicate with their target market virtually anywhere in the world. You need to introduce innovative ways to capture the attention of your target market to remain competitive in the market. All you need is a good marketing strategy that can attract your targeted niche and a competitive business. Some of the most far-reaching changes in IT managed service provider communication have been brought about by websites, email, social networking sites, and smartphones.
February 10, 2017
Anyone who starts a business is familiar with the concept of a business plan. This essential document is required to gain funding and shift a business from a bare-bones idea to a real-world operation. However, the business plan is just a starting point. If you want a business to remain open and operational, continuity planning is necessary. Continuity planning is the process in which a company identifies key business functions and the resources involved. It examines potential risk factors in order to develop a recovery plan, should the worst occur.
February 06, 2017
The concept of cloud computing appears omnipresent in our modern world as we rely on on-demand computing to manage our digital lives across multiple devices – mobiles, tablets, laptops, and so on – while at home, in the office, or on the move. This article introduces the key component in cloud computing and the servers that underpin each service and provide the computing resources, as well as describing how they provide some of cloud computing’s most notable benefits. Benefits of Cloud Computing The primary benefits of cloud computing are its cost savings,
February 03, 2017
Most business owners understand the need for professional IT support staff. Computer networks and online operations have become essential factors in running a modern business, and these technologies require advanced support for the purposes of productivity and security. That said, hiring on-site IT staff can be extremely expensive. Competing for the best and brightest employees may be beyond the means of many small businesses, or even their mid-sized brethren. With the onus on companies to provide the latest technological innovations for clients and consumers, as well as protect the private
January 30, 2017
As a business owner sometimes it becomes a hard task to determine when it is time to migrate or completely change your technology. However, it is beneficial to replace your outdated technology as much as possible. In fact, it’s one of the main ways of improving the quality of the services that you offer. One of the major things to recognize is that your company can quickly grow and thus it’s necessary for your IT department to direct funds and effort into the purchase of new systems as often as possible.
January 27, 2017
Operating in the online arena is a must for businesses looking to remain competitive. Unfortunately, the costs associated with computer and network security is untenable for some small businesses. The good news is many options are available at a variety of price points. Here are just a few options to explore when it comes to keeping your small business’s data safe. 1. Hire Help Having proper technical support on hand is a must if you want to protect your data. For many small businesses, the best option is to hire
January 23, 2017
Every business faces many common challenges. There are also potential risk factors that could cause significant setback, or even utter ruination, should they come to pass. It is enough to keep any business owner awake at night, worrying about the future. Preparedness is the key to mitigating risks, avoiding disaster when possible, and having a plan in place to cope and recover when unavoidable setbacks occur. Whether you are addressing computer security or natural disasters, having a business continuity plan in place is necessary. Hiring external help for this could,
January 20, 2017
Thirty years ago, the thought of hiring experts in networking and information technology was practically unheard of. These days, most businesses have little choice in the matter. The rapid advancement of new technology is something companies cannot afford to operate without. The average person has only a fraction of the knowledge needed to successfully manage a secure and efficient infrastructure of computers and networks. Modern business operations require highly trained experts in the IT field. There are a couple of different ways to go about procuring the services needed for
January 19, 2017
When the time is right for your business to bring on a managed service provider, there are several things to consider before signing a contract. Businesses both large and small have certain needs that are better managed by professionals. Contracting with a managed service provider allows owners and upper level management to focus their attention on growing and managing the business. Teaming up with a provider has several benefits if you choose the right partner. Conversely, bringing on a provider who doesn’t understand your needs or one that is unable to
December 26, 2016
Some say the planet is shrinking. The truth is over the last few hundred years, human population growth has been exponential. In more recent years, we’ve developed transportation options and communications technologies that allow people and cultures across the planet to connect, breaking down barriers to make way for a more aware and integrated society. This trend is only likely to become more pronounced as the spread of ideas begins to break down the walls of nationalism and a truly global community is born. For businesses, this shift has created
December 19, 2016
Just because you own and operate a vehicle doesn’t necessarily mean you have the time and inclination to become a seasoned auto mechanic. Instead, you simply take your car to a professional to have it serviced and deal with problems. As a business owner, you likely take the same approach to computer networks. You have other fish to fry, what with managing business operations. You don’t have the time or skill to take on technical support as well. The problem is hiring a professional network administrator and IT staff could
December 12, 2016
Protecting your business from virtual threats is becoming more complex by the day. If you want the best chances to avoid a data breach, you not only need proper security programs for your computer networks, but also policies and training procedures that will teach your employees how to behave in a safe and responsible manner when using your resources. Here are a few important IT policies every business should have. Password Protection It’s not enough to have a password protection program in place. A tool is only as good as
December 05, 2016
Every business owner knows that efficient and productive operations rely not only on skilled and dedicated workers, but also on the tools they have at their disposal. In this day and age, tools refer to technology and businesses that want to remain competitive have to be vigilant about keeping their tools up-to-date. For many small businesses working on a tight budget, this can pose a problem. Unfortunately, technology is advancing at ever-increasing speeds. Securing the latest and greatest computer networks, hardware, and programming can cost a pretty penny. That said,
November 30, 2016
Most businesses outsource all kinds of activities, from bookkeeping and accounting, to customer service, to materials supply, to shipping. There are several reasons to outsource. For one, keeping a full-time staff for rarely needed services is an inefficient use of funds. In addition, many companies simply can’t compete for top talent, so it’s easier to outsource to professional firms that can provide needed resources and specialists. When it comes to information technology (IT), which moves along at breakneck speeds, hiring qualified staff and keeping them trained in the latest advances
November 28, 2016
Modern businesses understand the need for security, not only in the traditional sense of securing a work facility, but also in the technological sense of securing computer networks. With data breaches more common than building break-ins these days, companies have much different security concerns than in generations past. What can you do to ensure the safety and security of your business on multiple fronts, both in the real world and the virtual one? Outsourcing could provide the solutions you’re seeking. Expert Services at Less Cost Whether you’re looking for cybersecurity
November 23, 2016
There are many occurrences that could disrupt your business, leading to loss of revenue and possibly additional, unplanned expenses. The biggest concern for many businesses used to revolve around inclement weather or natural disasters. These days, data breaches are a more immediate threat. Whatever the cause of disruption, however, a company’s ability to move ahead relies on having a solid business continuity plan in place to address the issue and recover in a timely manner. Here are a few tips to help you create a continuity plan for your operation.
October 17, 2016
There are so many potential jobs available in computer fields these days that it can be difficult to decide if you want work in computer networks or IT support, just for example. However, if you find that designing network architecture and implementing system plans fascinates and thrills you, a career in network engineering is probably the way to go. Some people prefer jobs later in the life cycles of networks – they would rather provide technical support or handle daily operations as network administrators. If you wish to puzzle out
October 10, 2016
No matter how much time, effort, and money you invest in product or service development, you simply can’t please every person all the time. There are going to be times when customers have questions and complaints that your company needs to address. When these customers contact you seeking help for their concerns, how will you handle it? Are you prepared to provide the answers they need or make repairs and reparations? Do you have the pieces in place to adequately support your products or services, and furthermore, to escalate the
October 03, 2016
Tech support is not just something that most businesses need; it’s something more and more companies must provide to their own customers. Whether your business sells smart home appliances, video games, or sonic screwdrivers, you will almost certainly have to provide technical support should something go awry with your products or services. Your ticketing system allows you to interact with customers who have questions or problems that need to be solved. However, a poorly integrated system could end up causing more harm than good. If your tech support ticketing system
September 27, 2016
Finding the right third-party IT support provider to partner with can make any business owner’s job easier. Most businesses struggle to keep up with technological advances and stave off threats like data breaches. The support and guidance offered by reputable and experienced IT professionals can alleviate worries and ensure network and computer security that helps to protect companies and their customers. The only question is: how do you find the right partner for your business? Here are a few factors you’ll want to consider before you choose a technical support
September 07, 2016
If you listen to people in the know, it’s not a matter of if your company will be the victim of a data breach, but when. Not only are most businesses (both large and small) woefully under-protected when it comes to system security, but hackers are finding more and more sophisticated ways to break in all the time. Of course, there are steps you can take to protect yourself from an attack, such as hiring a network administrator or computer security specialist to build appropriate security infrastructure and manage your
September 07, 2016
Even though the headlines often highlight major data breaches in corporations and government agencies, the truth is that the vast majority of businesses being hacked are small. Why is this the case? Because small businesses are generally under-protected. If hackers can break into huge corporations, with all the attention to cybersecurity, what’s to stop them from targeting smaller companies that can’t afford the same level of protection? The good news for small businesses is that adequate computer security is not beyond reach. Here are a few cybersecurity tips that can
September 07, 2016
For modern businesses, computer networks are the hub of operations. Without suitable hardware and software solutions, your business cannot hope to maintain the level of efficiency needed to compete. That said, how you run your network is just as important as the infrastructure you have in place. The value of appropriate technical support cannot be overstated, and you really need to engage in monitoring if you want to ensure efficient operations and a good experience for customers. Before you download software or hire just any monitoring firm, however, there are
September 07, 2016
Small business owners face a wide variety of challenges, often including insufficient staff, client dependence, and balancing a desire to create quality products with the need to increase quantity of sales, just for example. In truth, most of the biggest challenges small businesses commonly come up against revolve around one central theme: the bottom line. Many small businesses are struggling to grow on shoestring budgets, and their lack of capital makes for some tough decisions when it comes to allocating limited funds. Unfortunately, one area that small businesses tend to
August 09, 2016
We will be posting this with information about what is happening around AME Group.
April 21, 2016
Written by Dwayne Adams, AME Engineer Have you heard of Locky? It’s a cheery-sounding name, but it’s also a nickname of a new strain of Ransomware, which is a growing problem for all. This type of malware prevents or limits users from accessing their system. It forces its victims to pay the ransom through certain online payment methods in order to grant access to their systems or to get their data back. Some ransomware encrypts files (called Cryptolocker). Other types use TOR to hide C&C communications (called CTB Locker). How